Peer-to-peer-based VPN alternatives
ZeroTier
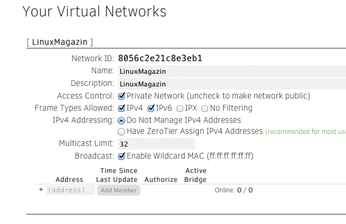
The last candidate in the field is ZeroTier. The project's first code on GitHub originates from mid-2013. ZeroTier generates an overlay network as a combination of software and service. The website, however, compares it with a WLAN. Peer-to-peer connections forward the data, similarly to Skype or BitTorrent. A virtual network is assigned one ID for identification, and there are public and private networks (Figure 6).

The software is available for download [4] for Linux, Mac OS X, and Windows 7. DEB and RPM packages are available for Linux, and a generic installer package is available for Intel's 32-bit and 64-bit architectures, as well as the Raspberry Pi. In the lab, I ran the installer on Gentoo Linux; the source code is available from a GitHub repository [10].
As with the other packages, you should first load the tun module. The init script you installed then starts the service. ZeroTier registers with the P2P network. You can manage ZeroTier connections using the zerotier-cli program; there is even a graphical interface for Windows and Mac OS X.
The zerotier-cli listpeers command will provide you with a list of connected nodes, and you should check whether the computer has found its way into the ZeroTier network. The output looks a bit like Listing 1. The status subcommand can also be used; however, it returns only the version, the specific node ID, and the Online or Offline status.
Listing 1
Output of zerotier-cli listpeers
The Earth network [11] with 8056c2e21c000001 as the ID is suitable for trying out the service for the first time. You should enter this via
zerotier-cli join 8056c2e21c000001
The listnetworks subcommand displays the connected networks and the connection status, and ifconfig -a references the zt0 for the first network.
The daemon did not configure an IP address for the interface in the test. There is, however, a network configuration in the /var/lib/zerotier/networks.d/ 8056c2e21c000001.conf file, including the IP address assigned by the network.
Users should proceed in public networks with the same precautions as in a public WLAN. This means: Firewall rules and encrypting the traffic using ZeroTier. A tcpdump on the zt0 interface immediately returned broadcast packets from other nodes. However, in contrast to the rest of the Internet, the ZeroTier tunnels are encrypted.
If users want to create a private network, they first need an account [12]. There they can, as shown in Figure 7, create a network and fine-tune the parameters. Private networks are free for up to 10 participants, ZeroTier asks for $4 per month for bigger networks. You need to enter the node IDs manually (from zerotier-cli info) or confirm them after a connection attempt, to make it impossible for all and sundry to join your private network.
ZeroTier is designed for easy operation. Participants may be able see who the client is communicating with, but they cannot control this. The technical and security FAQs [4] provide a good overview of how the network works and what algorithms it uses. ZeroTier provides an easy-to-use solution for users who want to bypass firewalls. However, this is a genuine headache for security admins who do not want tunneled connections. A quote on the homepage (Figure 8) shows which side the ZeroTier project takes.
Conclusions
The programs presented here are quite different from one another. Tinc and Freelan only work if the VPN user also controls the incoming Internet traffic, whereas this doesn't matter at all for IPOP and ZeroTier. A feature they all share is that they let you screen traffic from the eyes of the Internet and create direct links in the form of overlay networks and tunnels.
Tinc and Freelan stand up to comparison with established solutions such as OpenVPN, although Tinc has proved to be fairly impractical for larger networks because of its complex key distribution. In IPOP, the amount of time it takes to establish a connection can be a genuine pain – although maybe this just reflects the tester's impatience. The solutions cause worries in corporate security departments because they make it easy for users to undermine installed protection mechanisms.
Infos
- Tinc: http://www.tinc-vpn.org
- Freelan: http://www.freelan.org
- IPOP: http://ipop-project.org
- ZeroTier: http://www.zerotier.com
- Jabber: http://www.jabber.org
- Jingle: http://xmpp.org/extensions/xep-0166.html
- STUN RFC: http://tools.ietf.org/html/rfc5389
- TURN RFC: http://tools.ietf.org/html/rfc5766
- IPOP on GitHub: https://github.com/ipop-project/downloads/releases
- ZeroTier on GitHub: https://github.com/zerotier
- Earth network: https://www.zerotier.com/earth.html
- Admin account for ZeroTier: http://www.zerotier.com/admin.html
« Previous 1 2
Buy this article as PDF
(incl. VAT)
Buy Linux Magazine
Subscribe to our Linux Newsletters
Find Linux and Open Source Jobs
Subscribe to our ADMIN Newsletters
Support Our Work
Linux Magazine content is made possible with support from readers like you. Please consider contributing when you’ve found an article to be beneficial.

News
-
TUXEDO Computers Unveils Linux Laptop Featuring AMD Ryzen CPU
This latest release is the first laptop to include the new CPU from Ryzen and Linux preinstalled.
-
XZ Gets the All-Clear
The back door xz vulnerability has been officially reverted for Fedora 40 and versions 38 and 39 were never affected.
-
Canonical Collaborates with Qualcomm on New Venture
This new joint effort is geared toward bringing Ubuntu and Ubuntu Core to Qualcomm-powered devices.
-
Kodi 21.0 Open-Source Entertainment Hub Released
After a year of development, the award-winning Kodi cross-platform, media center software is now available with many new additions and improvements.
-
Linux Usage Increases in Two Key Areas
If market share is your thing, you'll be happy to know that Linux is on the rise in two areas that, if they keep climbing, could have serious meaning for Linux's future.
-
Vulnerability Discovered in xz Libraries
An urgent alert for Fedora 40 has been posted and users should pay attention.
-
Canonical Bumps LTS Support to 12 years
If you're worried that your Ubuntu LTS release won't be supported long enough to last, Canonical has a surprise for you in the form of 12 years of security coverage.
-
Fedora 40 Beta Released Soon
With the official release of Fedora 40 coming in April, it's almost time to download the beta and see what's new.
-
New Pentesting Distribution to Compete with Kali Linux
SnoopGod is now available for your testing needs
-
Juno Computers Launches Another Linux Laptop
If you're looking for a powerhouse laptop that runs Ubuntu, the Juno Computers Neptune 17 v6 should be on your radar.

