Subgraph OS – Adversary-resistant computing platform
Playing Coy
Special mention must go to Subgraph's own CoyIM instant messenger. CoyIM is designed to work with the XMPP message protocol, so you'll need to register an account with a compatible chat server to use it. (Figure 5). Connections are made via Tor + TLS to clearnet chat servers, although for extra security you may wish to consider using an XMPP provider that supports connecting via Tor hidden services, such as The Calyx Institute [5]. Where possible, the messenger will use the hidden service for a chat server, if it has a record of it.
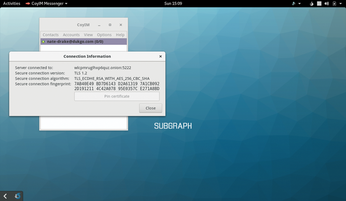
All conversations are encrypted via Off the Record (OTR) Messaging, which offers perfect forward secrecy – in other words, if the keys are compromised and a single conversation is decrypted, this won't help decrypt any of your other chats. On first run, CoyIM will ask you if you wish to encrypt your configuration file and if so, to choose a master password. You'll then be asked to either sign in or register your XMPP account. A green dot will appear next to your name once you're connected.
Like Subgraph itself, CoyIM has yet to undergo a full security audit, so use with caution.
Sub Rosa
Aside from hard work and a pat on the proverbial back from Snowden, Subgraph has much to offer the privacy-minded user.
Subgraph's website describes the OS as an "adversary resistant computer platform." The term adversary seems to have been interpreted broadly to include both hackers and government officials from oppressive regimes.
Users will notice this approach most when new programs are run: Subgraph Firewall will ask you to allow or deny the connection (Figure 6). You can also choose to permit a connection for only a certain amount of time. The default firewall policy of most Linux distros is to block incoming connections but allow all outgoing ones, so it's heartening to see that Subgraph polices connections on an application-by-application basis so seriously.
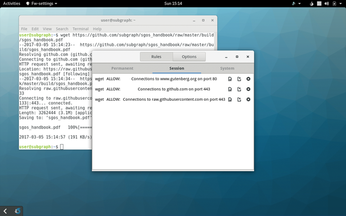
The Subgraph team discovered an excellent case in point when coding their firewall with Gnome Calculator. By default, this program will connect to various financial institutions online to gather currency exchange rates. This seems fairly harmless until you consider that searching for a specific currency could be used to determine which country you're in or about to travel to.
The Linux kernel used by Subgraph's latest release has been hardened with GrSecurity v4.8.15, which contains a number of privacy-related enhancements such as USB Lockout, a background process that denies all access to USB devices when the screen is locked or you're logged out.
GrSecurity also includes PaX – a set of patches that makes the kernel and userspace much less vulnerable to memory corruption exploits.
One form of memory corruption exploit, known as "stack smashing," is among the oldest and most reliable ways to hack into a system, whereby an adversary can execute arbitrary malicious code on your system.
PaX protects your computer from memory corruption exploits in a variety of ways. Chief among these is randomizing the layout of process memory, which makes it much more difficult for hackers to locate exactly where they've placed malicious code. It can also make memory pages non-executable. Payload stored in non-executable memory cannot run.
PaX also attempts to proactively kill applications that violate its security policies, hopefully preventing issues before they even arise [6].
The Wonderful Wizardry of Oz
Subgraph OS runs desktop applications inside the team's very own security sandbox named Oz. This builds on the protection offered by kernel hardening to protect your system from compromised applications.
On most mainstream Linux distributions, desktop applications running with the X11 display server can see and interact with each other. The Oz sandboxes prevent this by using Xpra, which renders individual applications with their own display server, so they cannot interact, improving security.
Oz can also restrict access to certain files, as well as network access and audio playback for applications that don't need it.
The actual sandboxing process works seamlessly for the user. Applications that are to be run in Oz are renamed, and a symbolic link is created in the original location of the program, which directs the system instead to the Oz binary. When the program is started, Oz automatically scans the program name and examines its associated policy document, which governs how the application launches and its run-time environment.
The Oz daemon then creates the sandbox and launches the real application safely inside it, as per the policy document. Outside the sandbox, an Xpra instance connects to the Xpra server inside the sandbox. This means the application cannot log keystrokes or otherwise meddle with applications [7].
The applications that run within the Oz sandboxes are those most likely to be exposed to untrustworthy networks and data, such as the Tor Browser and Evince PDF Reader. You can, however, enable Oz profiles for other applications by running the command:
sudo oz-setup install <program-name>
« Previous 1 2 3 Next »
Buy this article as PDF
(incl. VAT)
Buy Linux Magazine
Subscribe to our Linux Newsletters
Find Linux and Open Source Jobs
Subscribe to our ADMIN Newsletters
Support Our Work
Linux Magazine content is made possible with support from readers like you. Please consider contributing when you’ve found an article to be beneficial.

News
-
TUXEDO Computers Unveils Linux Laptop Featuring AMD Ryzen CPU
This latest release is the first laptop to include the new CPU from Ryzen and Linux preinstalled.
-
XZ Gets the All-Clear
The back door xz vulnerability has been officially reverted for Fedora 40 and versions 38 and 39 were never affected.
-
Canonical Collaborates with Qualcomm on New Venture
This new joint effort is geared toward bringing Ubuntu and Ubuntu Core to Qualcomm-powered devices.
-
Kodi 21.0 Open-Source Entertainment Hub Released
After a year of development, the award-winning Kodi cross-platform, media center software is now available with many new additions and improvements.
-
Linux Usage Increases in Two Key Areas
If market share is your thing, you'll be happy to know that Linux is on the rise in two areas that, if they keep climbing, could have serious meaning for Linux's future.
-
Vulnerability Discovered in xz Libraries
An urgent alert for Fedora 40 has been posted and users should pay attention.
-
Canonical Bumps LTS Support to 12 years
If you're worried that your Ubuntu LTS release won't be supported long enough to last, Canonical has a surprise for you in the form of 12 years of security coverage.
-
Fedora 40 Beta Released Soon
With the official release of Fedora 40 coming in April, it's almost time to download the beta and see what's new.
-
New Pentesting Distribution to Compete with Kali Linux
SnoopGod is now available for your testing needs
-
Juno Computers Launches Another Linux Laptop
If you're looking for a powerhouse laptop that runs Ubuntu, the Juno Computers Neptune 17 v6 should be on your radar.

