Tool Tips
GSmartControl 0.8.7
Function: Detects hard drive problems
Source: http://gsmartcontrol.sourceforge.net
License: GPLv3
Alternatives: Smartctl2

Thanks to S.M.A.R.T. (Self-Monitoring, Analysis, and Reporting Technology), users are made aware of hard disk problems before the data medium vociferously clamors for attention. The hardware collects various information depending on the connection and the type of medium. Linux users, for example, can read this information using the smartctl command-line tool. Those who prefer a bit more convenience should use the graphical interface GSmartControl.
The program uses smartctl in the background and can therefore handle the same query options for disks and solid-state drives. It identifies connected data media when launched and lists them – regardless of whether they are S.M.A.R.T.-capable. You can disable displaying uncooperative media in the configuration. You can also set individual parameters for each data medium.
GSmartControl provides information about the medium if you right-click on the corresponding icon. The detailed view has several tabs that you can use to access status indicators and logfiles. The tool highlights errors and threshold values. The Perform Tests tab lets you start various self-tests that can last between a few minutes and several hours. The program also lets you integrate smartctl output as virtual disks and therefore makes it easy to evaluate the collected data.
5 Stars GSmartControl is a practical graphical interface for smartctl and leaves nothing to be desired.
Pam_ihosts 1.1
Function: Access control by Pam module
Source: https://github.com/ColumPaget/pam_ihosts
License: GPLv3
Alternatives: Iptables

The PAM module restricts access to Linux computers. You can decide which hosts are allowed, either via the IP or MAC address or through regional association. However, actual user authentication needs to be working before Pam_ihosts has its say.
System administrators integrate the module into the computer's PAM configuration and edit the corresponding files in the /etc/pam.d directory. They can determine the behavior using various options. For example, there is a username or a list of accounts separated by commas in user. An * includes all, an ! allows a reversal, and allow-ip[s] and allow-mac[s] control access for specific IP or MAC addresses. IPv6 support is currently pending; Pam_ihosts only understands the IPv4 format. If the target machine has several network interfaces, administrators can specify the desired one in allow-def[s].
Admins also can allow or block specific regions. They can retrieve the information from the Regional Internet registries, which are linked from the Pam_ihosts documentation. These text files are in the configuration file at region-files; allow-region[s] lists one or more allowable ranges.
3 Stars Pam_ihosts is an interesting method for access control. As with all PAM extensions, care is need during the setup. There are deductions for the missing IPv6 support.
Rush 1.7
Function: Restrict shell access
Source: http://www.gnu.org/software/rush
License: GPLv3
Alternatives: Rbash, Rssh
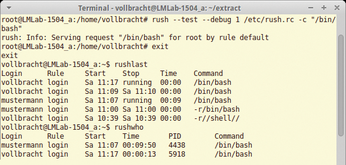
Using the restricted user shell, Linux administrators can define a limited range of functions with which their users can work at the command line. The GNU tool can be used as a login shell and is also well suited for chroot operations. The guide shows examples for accesses via scp, sftp, rsync, and svn.
The /etc/rush.rc configuration file contains the rules. System administrators can create them in a text editor of their choice. The key word rule initiates a new definition. Instructions behind this – such as command, uid, and match – define when a rule is activated. For some conditions, it is sufficient for the administrator to specify a match pattern that can also contain regular expressions. Other options such as transform, chroot, and chdir define the associated actions. For example, they rewrite the original command line, start a chroot environment, or cause a directory change.
Rush executes the first matching rule by default. With such fall-through statements, the tool searches for the next matching rule after executing the previous one. The tool maintains its own WTMP and UTMP files so that administrators can keep an eye on the use of Rush. The rushwho and rushlast commands evaluate them and write information to standard output.
4 Stars Rush provides lots of options for limiting access to the shell. However, creating a workable configuration is pretty time consuming and involves carefully studying the documentation.
« Previous 1 2
Buy this article as PDF
(incl. VAT)
Buy Linux Magazine
Subscribe to our Linux Newsletters
Find Linux and Open Source Jobs
Subscribe to our ADMIN Newsletters
Support Our Work
Linux Magazine content is made possible with support from readers like you. Please consider contributing when you’ve found an article to be beneficial.

News
-
TUXEDO Computers Unveils Linux Laptop Featuring AMD Ryzen CPU
This latest release is the first laptop to include the new CPU from Ryzen and Linux preinstalled.
-
XZ Gets the All-Clear
The back door xz vulnerability has been officially reverted for Fedora 40 and versions 38 and 39 were never affected.
-
Canonical Collaborates with Qualcomm on New Venture
This new joint effort is geared toward bringing Ubuntu and Ubuntu Core to Qualcomm-powered devices.
-
Kodi 21.0 Open-Source Entertainment Hub Released
After a year of development, the award-winning Kodi cross-platform, media center software is now available with many new additions and improvements.
-
Linux Usage Increases in Two Key Areas
If market share is your thing, you'll be happy to know that Linux is on the rise in two areas that, if they keep climbing, could have serious meaning for Linux's future.
-
Vulnerability Discovered in xz Libraries
An urgent alert for Fedora 40 has been posted and users should pay attention.
-
Canonical Bumps LTS Support to 12 years
If you're worried that your Ubuntu LTS release won't be supported long enough to last, Canonical has a surprise for you in the form of 12 years of security coverage.
-
Fedora 40 Beta Released Soon
With the official release of Fedora 40 coming in April, it's almost time to download the beta and see what's new.
-
New Pentesting Distribution to Compete with Kali Linux
SnoopGod is now available for your testing needs
-
Juno Computers Launches Another Linux Laptop
If you're looking for a powerhouse laptop that runs Ubuntu, the Juno Computers Neptune 17 v6 should be on your radar.

