The sys admin's daily grind: Whowatch et al.
On Patrol
For no particular reason, Charly occasionally patrols his server farm and hunts down attackers. He has put together a neat toolbox for this job.
Every server with an IP address on the Internet will receive uninvited visits at some point. The usual scans and scripted carpet bombing simply bounce off my machines thanks to clever firewalling, port knocking [1], and additional tools like Fail2ban [2]. To keep attackers from working around my defenses, I use two rootkit hunters: Rootkit Hunter [3] and Chkrootkit [4]. The latter, unfortunately, accuses my DHCP server of packet sniffing:
eth0: PACKET SNIFFER(/usr/sbin/dhcpd[28382])
This result is a known false positive, which I ignore. As an interim report, I can say that my varmint hunters have not seen any prey thus far.
Nevertheless, I occasionally go on patrol to see whether a server is behaving strangely. I like to use whowatch [5] for this purpose. This tool launches in the terminal with a process list; the second column shows me the owner. In the third column, Whowatch tells me whether the user is local or logged on via SSH, Telnet, or in some other way. For remote users, this information is followed by the IP address, and for local users, just :0.
Hotkey Control
I have two ways of navigating this information: I can use the arrow keys to select a line, press Enter, and see a tree view of the associated processes, as shown in Figure 1. Pressing O (owner) hides or displays the process owner; pressing D (details) creates a window with detailed information for the process.
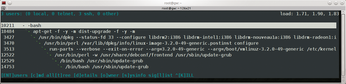
My second option is to type T (tree view) to show all running processes. In this tree view, too, pressing D will display more information. Pressing L (list of signals) shows me the control signals that I can send to the process, such as HUP, INT, TERM, and in an emergency KILL. I can display the overall system status, particularly in terms of memory management, by pressing S (sysinfo), which tells Whowatch to display the total load on the screen, in a style very much reminiscent of top (Figure 2).
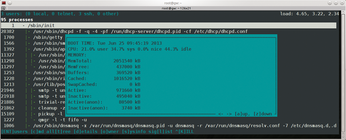
I have never found anything dangerous on my server patrols to date, but I do like that warm, safe, and cozy feeling.
Infos
- Fwknop: http://www.cipherdyne.org/fwknop/
- Fail2ban: http://www.fail2ban.org
- Rootkit Hunter: http://rkhunter.sourceforge.net
- Chkrootkit: http://www.chkrootkit.org (in Portuguese)
- Whowatch: http://whowatch.sourceforge.net
Buy this article as PDF
(incl. VAT)
