Nine steps for securing an Android tablet
Set One App for One Function
The average tablet includes so many services that some are redundant. For example, a book downloaded from the Play Store is read within the Play Store, whereas ones downloaded from Kobo or Kindle are each downloaded in separate apps. Similarly, the manufacturer often offers a web browser, even though Chrome is bundled with the tablet.
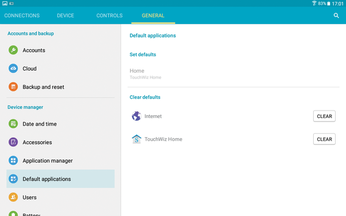
In the interests of minimizing access, set default applications for each function whenever possible, and uninstall the rest. You may be unable to delete default apps without rooting your tablet (see below), but most can be disabled, if nothing else (Figure 6).
Replace the Default Mail App
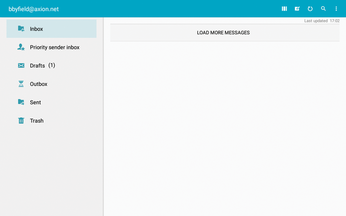
Email has always been a major source of malware, to say nothing of spam. However, the default email reader on most tablets offers no anti-spam or filtering, although it does allow signed and encrypted email. Check the Play Store for an alternative mail app that includes security features (Figure 7). Alternatively, exclusively use Gmail, which is probably already installed, and disable the default reader.
Root Your Device or Install CyanogenMod
As you explore your tablet, you may notice that your account has limited access. For example, you cannot view some directories on the hard drive such as /sbin or delete some default apps. Neither can you delete the unsecured Guest user account or install an effective firewall.
Technophiles and consumer advocates alike decry this situation. As a result, third-party tools have been developed for rooting – that is, for getting full root access on Android devices (on iOS devices, the same process is called jailbreaking).
Rooting's legal status varies with your location. It may invalidate your warranty in some areas, and it runs a small risk of making your tablet permanently useless. For these reasons, you should research rooting thoroughly before attempting it, searching the Internet for specific instructions for your tablet's manufacturer, model, and Android version. You might also want to look for first-hand accounts of rooting to determine your odds of success.
If you do root your tablet, you will be able not only to use apps that require rooting, which include more thorough security, but also to explore the Android operating system more thoroughly. After rooting, you might want to install a terminal emulator, as well as vi or emacs to help you explore.
As an alternative to rooting your tablet, consider modding, that is, installing CyanogenMod [1], an open source version of Android. CyanogenMod has the same benefits and risks as rooting, but it comes with an installer that automates the install process. Both rooting and installing CyanogenMod will give you the final degree of control you need to make your tablet secure.
« Previous 1 2 3 4 Next »
Buy this article as PDF
(incl. VAT)
Buy Linux Magazine
Subscribe to our Linux Newsletters
Find Linux and Open Source Jobs
Subscribe to our ADMIN Newsletters
Support Our Work
Linux Magazine content is made possible with support from readers like you. Please consider contributing when you’ve found an article to be beneficial.

News
-
TUXEDO Computers Unveils Linux Laptop Featuring AMD Ryzen CPU
This latest release is the first laptop to include the new CPU from Ryzen and Linux preinstalled.
-
XZ Gets the All-Clear
The back door xz vulnerability has been officially reverted for Fedora 40 and versions 38 and 39 were never affected.
-
Canonical Collaborates with Qualcomm on New Venture
This new joint effort is geared toward bringing Ubuntu and Ubuntu Core to Qualcomm-powered devices.
-
Kodi 21.0 Open-Source Entertainment Hub Released
After a year of development, the award-winning Kodi cross-platform, media center software is now available with many new additions and improvements.
-
Linux Usage Increases in Two Key Areas
If market share is your thing, you'll be happy to know that Linux is on the rise in two areas that, if they keep climbing, could have serious meaning for Linux's future.
-
Vulnerability Discovered in xz Libraries
An urgent alert for Fedora 40 has been posted and users should pay attention.
-
Canonical Bumps LTS Support to 12 years
If you're worried that your Ubuntu LTS release won't be supported long enough to last, Canonical has a surprise for you in the form of 12 years of security coverage.
-
Fedora 40 Beta Released Soon
With the official release of Fedora 40 coming in April, it's almost time to download the beta and see what's new.
-
New Pentesting Distribution to Compete with Kali Linux
SnoopGod is now available for your testing needs
-
Juno Computers Launches Another Linux Laptop
If you're looking for a powerhouse laptop that runs Ubuntu, the Juno Computers Neptune 17 v6 should be on your radar.

