Tools to prevent drive-by attacks
Upgrading the Gateway
The defense framework should not focus solely on the client. Another important component in your anti-malware strategy is the border to the Internet.
The first and most important measure should be to enable a web filter on your Internet gateway or – if the type of firewall you use doesn't support this – to install an additional web proxy with appropriate URL filtering. If you use Squid, SquidGuard is a useful URL redirector that is available for free; also, free blacklists are available for SquidGuard [26]. However, the free blacklists are often maintained as amateur projects; current malware domains are therefore more likely not to be found on these lists. Commercial providers have a clear lead in this area.
Graphical Firewalls
The term "graphical firewall" often refers to a security system consisting of a UTM firewall and a terminal server. The terminal server is connected to a separate network interface on the firewall, and it is thus isolated from the LAN in a demilitarized zone (DMZ; Figure 5). For the users on the LAN, all Internet-facing network connections are now blocked on the firewall and are only accessible through a graphical protocol (hence the name) on the terminal server in the DMZ. Methods for terminal server access include protocols such as VNC, RDP, PC-over-IP, SPICE, NX, and ICA, but also X11 tunneling.
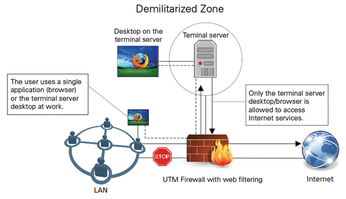
The user then launches the browser and possibly other Internet software on the terminal server, for which Internet access is enabled on the firewall. Ideally, as a further protective measure, the firewall will additionally run a web proxy with URL filtering and virus scanning enabled. The user on the terminal server should be created according to the principle of least possible privileges. Now, if the browser or one of the plugins is attacked by drive-by download, damage to the session on the terminal server is limited – the attacker first has to compromise the terminal server and the firewall to gain access to the actual client on the LAN.
You'll find instructions for building a graphical firewall in Building Internet Firewalls on the O'Reilly site [27]. The German Federal Office for Information Security (BSI) introduced the concept of the Remote-Controlled Browser System (ReCoBS) [28] a few years ago to describe the principle of outsourcing the browser to a terminal server using a graphical firewall.
Professional graphical firewalls include the TightGate Pro product and secureVD. According to the manufacturer, TightGate Pro [29] is suitable for user groups with at least 10 seats, particularly in regulated environments such as government offices. SecureVD [30] (Figure 6) is based on a UTM firewall; its hardened operating system was extended to include a KVM hypervisor, which means you can launch virtual machines running Windows or Linux directly on the firewall using the web-based administration interface. The virtual network adapters of the virtual machines are connected to the physical DMZ interface of the firewall through a bridge so that the virtual machines are also isolated in the DMZ. SecureVD can, in principle, virtualize both servers (e.g., web, FTP, and mail servers) as well as desktops.

Because secureVD supports desktop virtualization for both Linux and Windows, users can work with familiar software. If the virtual Windows desktop also has an RDP server (e.g., the XP/VS Terminal Server for Windows by Thinstuff [31]), multiple users can easily share a single virtual desktop.
Starting with the standard version, the Thinstuff XP/VS Terminal Server also supports TSX RemoteApp (seamless windows), which means that the browser or any other application can be started via an RDP connection from the virtual machine and then displayed directly at the workplace. This removes the need to use two desktops, which many users find confusing.
Conclusions
Drive-by downloads are already the method of choice for spreading malware. A complete solution to this problem is currently not in sight, so admins need to deal with this issue urgently. However, the situation is far from hopeless; armed with a suitable mix of tools and techniques, administrators can counter the threat.
Infos
- ENISA Threat Landscape: http://www.enisa.europa.eu/activities/risk-management/evolving-threat-environment/ENISA_Threat_Landscape/at_download/fullReport
- Java attacks: http://community.websense.com/blogs/securitylabs/archive/2013/03/25/how-are-java-attacks-getting-through.aspx
- Websense 2012 Threat Report: http://www.websense.com/content/websense-2012-threat-report-download.aspx
- BackTrack: http://www.backtrack-linux.org
- Kali Linux: http://www.kali.org
- Common Exploit Kits: http://3.bp.blogspot.com/-uyMLGw7f0SI/UKAPwmIjc4I/AAAAAAAAFlw/_tGdzXgfYnI/s1600/1780x1200_CommonExploitPacks2012u18.jpg
- ExploitPackTable 2013: https://docs.google.com/spreadsheet/ccc?key=0AjvsQV3iSLa1dE9EVGhjeUhvQTNReko3c2xhTmphLUE#gid=0
- CVE: http://cve.mitre.org
- BSI catalog of measures: https://www.bsi.bund.de/SharedDocs/Downloads/DE/BSI/Publikationen/Studien/WebSec/WebSec_pdf.pdf?__blob=publicationFile (in German)
- Fortify: http://en.wikipedia.org/wiki/Fortify_Software
- IBM Security AppScan: http://www-03.ibm.com/software/products/us/en/appscan/
- Skipfish: http://code.google.com/p/skipfish
- What is Safe Browsing? https://developers.google.com/safe-browsing
- Safe Browsing API: http://www.google.com/safebrowsing/diagnostic?site=mysite.com
- Malware domain list: http://www.malwaredomainlist.com/mdl.php
- InitiativeS: https://www.initiative-s.de/en/index.html
- Wepawet: http://wepawet.iseclab.org/
- ModSecurity: http://www.modsecurity.org
- Mozilla plugin check: https://www.mozilla.org/en-US/plugincheck
- Qualys BrowserCheck: https://browsercheck.qualys.com
- Qualys Business Edition: http://www.qualys.com/forms/browsercheck-business-edition
- F-Secure: http://www.f-secure.com/en/web/business_us
- Protection Service for Business, Workstation http://download.f-secure.com/webclub/supported%20applications.pdf
- BLADE: http://www.blade-defender.org/eval-lab
- Sirrix AG: http://www.sirrix.com/content/pages/home_en.htm
- SquidGuard: http://www.squidguard.org/blacklists.html
- Building Internet Firewalls: http://docstore.mik.ua/orelly/networking_2ndEd/fire/ch18_03.htm
- ReCoBS: http://www.commoncriteriaportal.org/files/ppfiles/pp0040b.pdf
- TightGate Pro: http://www.m-privacy.de/produkte/tightgate-pro (in German)
- secureVD: http://www.endian.com/us/partner/oem/securevd/
- XP/VS terminal server: http://www.thinstuff.de/products/xpvs-server
« Previous 1 2 3
Buy this article as PDF
(incl. VAT)
Buy Linux Magazine
Subscribe to our Linux Newsletters
Find Linux and Open Source Jobs
Subscribe to our ADMIN Newsletters
Support Our Work
Linux Magazine content is made possible with support from readers like you. Please consider contributing when you’ve found an article to be beneficial.

News
-
TUXEDO Computers Unveils Linux Laptop Featuring AMD Ryzen CPU
This latest release is the first laptop to include the new CPU from Ryzen and Linux preinstalled.
-
XZ Gets the All-Clear
The back door xz vulnerability has been officially reverted for Fedora 40 and versions 38 and 39 were never affected.
-
Canonical Collaborates with Qualcomm on New Venture
This new joint effort is geared toward bringing Ubuntu and Ubuntu Core to Qualcomm-powered devices.
-
Kodi 21.0 Open-Source Entertainment Hub Released
After a year of development, the award-winning Kodi cross-platform, media center software is now available with many new additions and improvements.
-
Linux Usage Increases in Two Key Areas
If market share is your thing, you'll be happy to know that Linux is on the rise in two areas that, if they keep climbing, could have serious meaning for Linux's future.
-
Vulnerability Discovered in xz Libraries
An urgent alert for Fedora 40 has been posted and users should pay attention.
-
Canonical Bumps LTS Support to 12 years
If you're worried that your Ubuntu LTS release won't be supported long enough to last, Canonical has a surprise for you in the form of 12 years of security coverage.
-
Fedora 40 Beta Released Soon
With the official release of Fedora 40 coming in April, it's almost time to download the beta and see what's new.
-
New Pentesting Distribution to Compete with Kali Linux
SnoopGod is now available for your testing needs
-
Juno Computers Launches Another Linux Laptop
If you're looking for a powerhouse laptop that runs Ubuntu, the Juno Computers Neptune 17 v6 should be on your radar.

