Managing port security
Discovering Hidden Ports
Security breaches often go unnoticed because they use hidden ports. You can discover any hidden ports using the unhide utility. Two versions are available online, the general unhide command and the more specific unhide-tcp. Both have similar functions, but it appears that unhide-tcp may be obsolete. Usually, it is wise to run unhide with the -f option, which generates a text log called unhide-linux.log in the current directory so you can refer back to the output.
The unhide utility uses several techniques, which are entered as sub-commands after the main command, without any hyphens. Some techniques may take several minutes to run. The techniques include:
- The
brutetechnique: Checks every process ID. It should be run twice using the-doption to avoid false positives, such as an application running at the command line. A false positive may occur when a temporary process uses a port, and it should disappear when the process finishes. You may want to repeat this command several times to ensure that the temporary process has finished. In the documentation, this choice is called the brute force option (Figure 6).

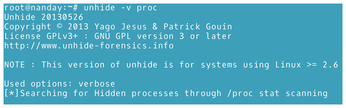
- The
proctechnique: Compares/procwith/bin/ps. On a clean system, the output of the two directories should match. It may be helpful to add the-voption for verbose output (Figure 7).
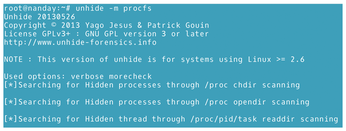
- The
procfstechnique: Compares information from/procfsand/bin/ps. Add the-moption to run additional tests (Figure 8).
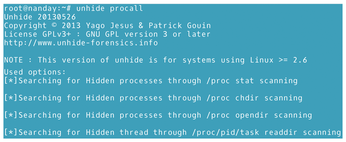
- The
procalltechnique: Combines theprocandprocfstests (Figure 9).
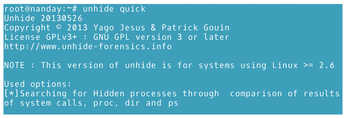
- The
quicktechnique: Combines theproc,procfs, andsystechniques and is about 20 times faster. The speed may result in more false positives, so the techniques might need to be run separately afterwards (Figure 10).
- The
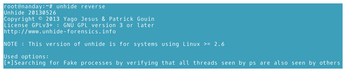
reversetechnique: Checks that all threads in/bin/psare also in/procfsand seen by system calls. This technique is specifically designed to see if a rootkit is making/bin/psshow a fake process (Figure 11).
- The
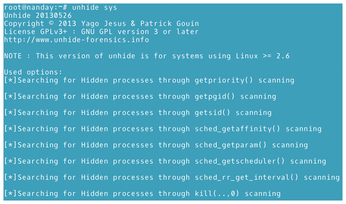
systechnique: Compares information gathered from/bin/pswith information gathered from system calls (Figure 12).
When using unhide, be prepared to run several tests. Run the quick technique first and then other techniques to eliminate any false positives. The reverse technique also returns speedy results. As an extra precaution, run other tests to confirm the results.
Levelling Up
I've covered the basic commands for working with ports. You'll find many of these commands installed with sets of utilities, and all commands should be found in the repositories of most distributions. For large networks, you also might want to install nmap. nmap does numerous tests, but when checking ports it provides an interesting ports table, which lists the port number and protocol, service name, and the port's state (open, closed, filtered, or unfiltered – filtered meaning that a firewall or other network element blocks the port). However, nmap is often overkill. For small networks or standalone systems, the commands described in this article should be more than adequate for controlling ports.
Infos
- Default port numbers: https://geekflare.com/default-port-numbers/
« Previous 1 2
Buy this article as PDF
(incl. VAT)
Buy Linux Magazine
Subscribe to our Linux Newsletters
Find Linux and Open Source Jobs
Subscribe to our ADMIN Newsletters
Support Our Work
Linux Magazine content is made possible with support from readers like you. Please consider contributing when you’ve found an article to be beneficial.

News
-
Canonical Releases Ubuntu 24.04
After a brief pause because of the XZ vulnerability, Ubuntu 24.04 is now available for install.
-
Linux Servers Targeted by Akira Ransomware
A group of bad actors who have already extorted $42 million have their sights set on the Linux platform.
-
TUXEDO Computers Unveils Linux Laptop Featuring AMD Ryzen CPU
This latest release is the first laptop to include the new CPU from Ryzen and Linux preinstalled.
-
XZ Gets the All-Clear
The back door xz vulnerability has been officially reverted for Fedora 40 and versions 38 and 39 were never affected.
-
Canonical Collaborates with Qualcomm on New Venture
This new joint effort is geared toward bringing Ubuntu and Ubuntu Core to Qualcomm-powered devices.
-
Kodi 21.0 Open-Source Entertainment Hub Released
After a year of development, the award-winning Kodi cross-platform, media center software is now available with many new additions and improvements.
-
Linux Usage Increases in Two Key Areas
If market share is your thing, you'll be happy to know that Linux is on the rise in two areas that, if they keep climbing, could have serious meaning for Linux's future.
-
Vulnerability Discovered in xz Libraries
An urgent alert for Fedora 40 has been posted and users should pay attention.
-
Canonical Bumps LTS Support to 12 years
If you're worried that your Ubuntu LTS release won't be supported long enough to last, Canonical has a surprise for you in the form of 12 years of security coverage.
-
Fedora 40 Beta Released Soon
With the official release of Fedora 40 coming in April, it's almost time to download the beta and see what's new.

