A command-line network intrusion detection system
Running Snort
When Snort is configured and validated, you can run it with a single-use command:
snort -d -l /var/log/snort/ -h IP-ADDRESS -A console-c /etc/snort/snort.conf
Note that this command is a general purpose command for sniffing packets at the designated IP address, writing the log to standard output (-A console), as well as a file (-l), and using the listed configuration file (-c). The output starts with a copyright notice, followed by a description of the rules used and a listing of any rules that are obsolete or missing, and, finally, an ongoing list of events on the IP address.
Individual log entries begin with the date and the time, followed by the activity, its classification, and the source of the activity. An activity is given a priority number, generally on a scale of 1 (severe) to 4 (mild), although you can assign priorities as high as you wish when you write or modify a rule. If you are new to packet sniffing, you may be alarmed at the frequency and persistency of activities on a modern computer, so remember that Snort logs all packet activity, not just potentially suspicious activity, and is only as good as the installed rules. False positives will be common (Figure 7). Log entries are also written to /var/log/snort.
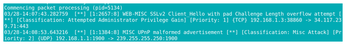
Most likely, though, you will want Snort to be running all the time, especially on a network. If your system uses systemd, create and edit as root the file /lib/systemd/system/snort.service and include the code provided in Listing 1 to the file.
Listing 1
Editing /lib/systemd/system/snort.service
[Unit] Description=Snort NIDS Daemon After=syslog.target network.target [Service] Type=simple ExecStart=/usr/local/bin/snort -q -u snort -g snort -c /etc/snort/snort.conf -i eth0 [Install] WantedBy=multi-user.target
Save the file, and then reload systemctl with:
systemctl daemon-reload
Snort will then be started at login or with the command:
systemctl start snort
Further Information
I have provided a bare bones outline for getting Snort ready to use. The Snort man page includes dozens of options. Trying to detail all the options here would be unrealistic. For further information, consult the latest Snort documentation [6] – which, despite the title displayed, is intended for version 3.0, not version 2.9.16. Snort is a mature piece of software that addresses complex issues, so be prepared to invest considerable time and experimentation if you want to get the most from it.
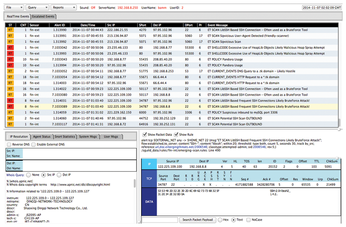
If you want to learn more about intrusion detection but prefer a desktop environment, spend some time with Sguil (Figure 8). Sguil relies heavily on Snort but also includes a number of related tools, including Barnyard2, tcpdump, and Wireshark. However, because Snort heavily comments its configuration files, it may be all you need to protect your system to your satisfaction. Where you go from here is up to you.
Infos
- Snort: https://www.snort.org/
- "The greatest open source software of all time" by Doug Dineley, InfoWorld, August 17, 2009: https://www.infoworld.com/article/2631146/the-greatest-open-source-software-of-all-time.html
- Snort download: https://www.snort.org/downloads
- Rule structure: https://cyvatar.ai/write-configure-snort-rules/
- Test rule: https://upcloud.com/community/tutorials/installing-snort-on-debian/
- Documentation: http://manual-snort-org.s3-website-us-east-1.amazonaws.com
- Sguil: http://bammv.github.io/sguil/index.html
« Previous 1 2
Buy this article as PDF
(incl. VAT)
Buy Linux Magazine
Subscribe to our Linux Newsletters
Find Linux and Open Source Jobs
Subscribe to our ADMIN Newsletters
Support Our Work
Linux Magazine content is made possible with support from readers like you. Please consider contributing when you’ve found an article to be beneficial.

News
-
Canonical Releases Ubuntu 24.04
After a brief pause because of the XZ vulnerability, Ubuntu 24.04 is now available for install.
-
Linux Servers Targeted by Akira Ransomware
A group of bad actors who have already extorted $42 million have their sights set on the Linux platform.
-
TUXEDO Computers Unveils Linux Laptop Featuring AMD Ryzen CPU
This latest release is the first laptop to include the new CPU from Ryzen and Linux preinstalled.
-
XZ Gets the All-Clear
The back door xz vulnerability has been officially reverted for Fedora 40 and versions 38 and 39 were never affected.
-
Canonical Collaborates with Qualcomm on New Venture
This new joint effort is geared toward bringing Ubuntu and Ubuntu Core to Qualcomm-powered devices.
-
Kodi 21.0 Open-Source Entertainment Hub Released
After a year of development, the award-winning Kodi cross-platform, media center software is now available with many new additions and improvements.
-
Linux Usage Increases in Two Key Areas
If market share is your thing, you'll be happy to know that Linux is on the rise in two areas that, if they keep climbing, could have serious meaning for Linux's future.
-
Vulnerability Discovered in xz Libraries
An urgent alert for Fedora 40 has been posted and users should pay attention.
-
Canonical Bumps LTS Support to 12 years
If you're worried that your Ubuntu LTS release won't be supported long enough to last, Canonical has a surprise for you in the form of 12 years of security coverage.
-
Fedora 40 Beta Released Soon
With the official release of Fedora 40 coming in April, it's almost time to download the beta and see what's new.

