User commands and logs
Keeping Log

Many logging and user-related commands can help you check on your system and keep track of security matters. We guide you through several helpful tools.
You can tell that Unix and Linux were designed for multiple logins by all the logs and commands that provide information about users. These tools often detect the first signs of an attempt to break into your system. In an institutional environment, they can be used to check not only what resources are being used but also whether users are doing what they are supposed to be doing.
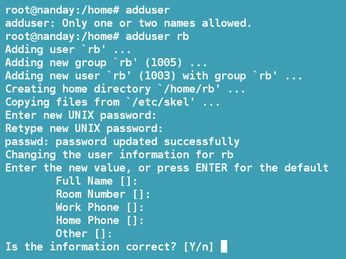
If you have done any systems administration at all, you have probably used the adduser command. The adduser command (Figure 1) provides a simple wizard to help you create a new account. By default, much of the work is done for you, such as automatically creating a user ID (UID). However, you can choose to specify many details for yourself with options like --gid ID and --shell SHELL.
[...]
Buy this article as PDF
(incl. VAT)