Klaus Knopper answers your Linux questions
Ask Klaus!

UEFI Workaround
Dear Klaus, Please help! I have done everything I can think of to install Linux on my 2013 touchscreen Asus Visiobook. I partitioned the hard drive, and I am using a Live USB, and I also installed the latest Linux kernel. When I reboot, I get the option to launch Ubuntu or Windows, but every time I try to choose Ubuntu, I am denied! Please help, I hate Windows 8. What can I do? Or, what didn't I do?
Sincerely, David
Answer
A more precise error message would be helpful, although it could well be that there is none and you are just thrown back to the boot choice menu, which is what your question suggests. But, I will try to find an explanation and a possible solution anyway.
First, I assume that it is an Asus Vivobook – at least, that's the model name that would closely match your description. This notebook is known to have certain complications concerning the preset boot mode for Windows 8, which may look hopeless at first if you have followed the Ubuntu forums thread [1].
So, you tried to run the Ubuntu "Windows installer," and it seems that installation of Ubuntu basically went OK, and a menu loader was installed, either the Windows one (using the WUBI Ubuntu installer, or the native method with GRUB 2). Now, if the boot menu throws you back to the menu instead of booting Ubuntu, or the system gets stuck with an error message, you may have hit the "secure boot" UEFI problem.
"Secure Boot" is a misnomer; it means that starting an operating system on this computer is impossible if the OS is not digitally signed by someone whose digital signature certificate is present in an internal list of "allowed vendors." Depending on the BIOS, booting from a "legacy" device like DVD may still be supported independently of UEFI, but any bootloader or OS installed on disk will fail to boot if it's not among the "allowed" ones [2].
Even if you use the "Windows installer" of Ubuntu, which should add an entry in the Windows bootloader for starting Ubuntu from it, "Secure boot" may keep the selected OS from starting.
Solution: Part of the UEFI standard includes the possibility of switching off "Secure boot" and using the standard BIOS disk boot record method, instead of booting from an EFI partition. This mode is called the "Compatibility Support Module" (CSM) and is labeled "Launch CSM" in the Asus Vivobook's BIOS setup, which you can reach by hitting F2 quickly and repeatedly during the first milliseconds after turning on the computer, then entering the BIOS settings.
Besides enabling the CSM, you should disable "Fast boot" in the BIOS, because this keeps some devices like USB flash disks from booting. To boot a Live system or installation DVD directly, CSM also should be enabled and "Fast boot" disabled.
With this BIOS setting, it should be possible to boot directly from any Linux distribution medium, even from an external USB DVD drive, with no problems.
Unfortunately, the preinstalled Windows is most likely preset to require the EFI Secure Boot mode, so it will stop booting from hard disk once you switch to CSM. Some computers have a hybrid UEFI and CSM mode where they can do both, but yours only seems to support one or the other, so if you want both Linux and Windows on your computer and don't want to switch back and forth between UEFI "secure" and standard boot mode, this is what you need to do:
- Enable CSM launch and disable "Fast Boot" in the BIOS, as mentioned above.
- Wipe the hard disk partitioning, perhaps using a Linux Live system or the Ubuntu installation DVD in rescue mode, and add a Windows partition. You will lose all data on the disk, so make sure you have a backup of everything important. Set the partitioning tool to use a master boot record (MBR; MS-DOS) partition table, not GUID/GPT for EFI. If you would like to stay compatible with Windows 8 defaults, create the first partition as 1GB FAT32 formatted, and the second partition as NTFS with a size of at least 30GB for Windows. Leave enough empty space for installing Ubuntu later, or create a swap partition of 1GB or more and one or more additional ext4 partitions that cover the rest of the disk. Windows should just ignore these.
- Run the Windows installation in CSM boot mode from an installation medium. Do NOT use the "recovery" procedure described in your computer's manual. You will need the "product key" on the sticker that sits on the bottom side of your notebook. Check that Windows will boot afterwards without complaining about UEFI. It should have left the empty Linux partitions as they are. If it asks you to format them at any time, deny and tell the dialog to remember that choice!
- Run the Linux installation from an installation medium, also in CSM mode, and tell the installer to reuse the swap and Linux partitions you already created. Or, create new ones on the empty space of the disk, leaving the Windows installation intact. Running installations in this order is safer, because Windows tends to destroy boot records of other operating systems during installation, whereas Linux adds an entry for other OSs on the MBR.
Now you should have a working dual-boot Windows/Linux setup with no more Secure Boot pains.
As far as forums tell, the Vivobook's hardware is supported by the latest Ubuntu version, so you should not have to upgrade the kernel after installation.
Configuring S/MIME in mutt
Klaus: Thank you for your article in October 2013 [3]. Please share which distro you were using? I have attempted with mutt 1.5.20 and 1.5.21 packages (.deb) on Squeeze and Wheezy. Found several known bugs. Google has given some How-To's without joy. Mutt in Knoppix 7.0 seems to be configured without OpenSSL. I would try another distro, but most are shipping mutt 5.5.21 or earlier.
Thanks, Charles
Answer
I actually used Knoppix for the tests, which is based on Debian. Mutt came from Debian/unstable, so it has all the newest features included (mainly the necessary configuration keywords for S/MIME). To be sure, it's not a version I compiled on my own, I just retried with mutt 1.5.21-6.4 now from Debian/testing.
Mutt is not compiled/linked with OpenSSL; your observation is correct, but this is just because it's not directly using any OpenSSL libs or procedures. For connecting encrypted to IMAPS or POP3s servers via SSL or TLS, the GnuTLS library is used.
For S/MIME mail (SSL encrypted and signed mail content), mutt calls the openssl command as an external handler, and pipes the mail messages through it. This is what the .muttrc configuration lines mentioned in Linux Magazine issue 155 will do, so don't worry if ldd or the package dependencies shown with dpkg -s mutt don't mention any libssl or openssl references in mutt; it's not required there. Even /usr/bin/smime_keys, which comes with mutt and which manages certificates, is just a Perl program that calls openssl.
Just install OpenSSL (the front-end program) to get S/MIME support in mutt, add the OpenSSL commands from issue 155 to .muttrc (Listing 1), and your mutt should be ready.
Listing 1
Settings for Handling S/MIME Attachments
set smime_default_key="<your smime key file ID>" set smime_ca_location="~/.smime/ca-bundle.crt" set smime_certificates="~/.smime/certificates" set smime_keys="~/.smime/keys" set smime_pk7out_command="openssl smime -verify -in %f -noverify -pk7out" set smime_get_cert_command="openssl pkcs7 -print_certs -in %f" set smime_get_signer_cert_command="openssl smime -verify -in %f -noverify -signer %c -out /dev/null" set smime_get_cert_email_command="openssl x509 -in %f -noout -email" set smime_import_cert_command="smime_keys add_cert %f" set smime_encrypt_with="des3" set smime_encrypt_command="openssl smime -encrypt -%a -outform DER -in %f %c" set smime_sign_command="openssl smime -sign -signer %c -inkey %k -passin stdin -in %f -outform DER" set smime_decrypt_command="openssl smime -decrypt -noverify -passin stdin -inform DER -in %f -inkey %k -recip %c" set smime_verify_command="openssl smime -verify -inform DER -in %s -content %f -noverify" set smime_verify_opaque_command="openssl smime -verify -inform DER -in %s -noverify"
Finding Partitions
Hello Klaus: My problem seems to be how Linux thinks of my hard drive partitions (Figure 1; I am using Linux Mint 15, 64-bit Cinnamon). I have a partition for data, labeled Data on one drive. That partition does not show up at all now until I go into Computer on my desktop and open it, then click on it. The other partitions seem unaffected. The partition is NTFS because I use Windows 7 when I must, and Windows is too stupid to read any Linux format disk! And, sometimes I need to have Windows access the partition.

I have a 3TB WD "Book" external drive that takes USB3, which I only connect when I want to do a backup to it. It has a Data folder also. Could that have confused Linux? Figure 2 is what GParted shows.
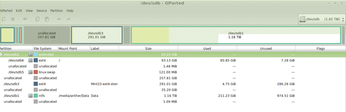
Your advice will be much appreciated, Tony
Answer
In your screenshot, the partitioning looks OK, and the /dev/sdb1 NTFS partition has the "Data" label you mentioned. The 2TB disks can still be fully accessed with the MBR partition table type that you use. With larger disks, you will have to switch to GPT partitioning unless the disk has a sector size larger than 512 bytes.
The desktop file manager usually fetches partition names from a label or just displays the partition names (sda1 for the first partition on the fist disk, sdb1 for the first partition on the second disk, and so on). Because MS-DOS partition tables have no entry for a "partition label," this label is being read from the filesystem contained in the partition. You can try
sudo blkid /dev/sdb1
to find out what blkid knows about the filesystem on partition /dev/sdb1. If the output contains a LABEL= item, the filesystem label should also be detectable by udev, which uses blkid internally.
Udev also creates the contents of /dev/disk/by-label containing symlinks from filesystem labels to the real partitions, which may also be used by the file manager to display "named partitions." If blkdev shows no label, this can mean that the support for NTFS filesystems is incomplete or does not exist in blkid and its associated libraries. Compare this with FAT32 partitions that have a label; they should always be found.
Alternatively, you can add an entry to /etc/fstab to ensure that the partition can be mounted by an unprivileged user:
/dev/sdb1 /media/sdb1 ntfs-3g user,umask=000
With this entry, you can simply mount the NTFS partition with
mount /media/sdb1
Note that the mountpoint must exist and be owned by the unprivileged user. Chances are that your file manager also looks into /etc/fstab to find "unnamed" partitions.
Infos
- Installing Ubuntu 13.10 with Windows 8 on Asus Vivobook: http://ubuntuforums.org/showthread.php?t=2146936
- UEFI: http://en.wikipedia.org/wiki/Unified_Extensible_Firmware_Interface#Secure_boot
- Adding Encryption to Mutt in "Ask Klaus!" Linux Pro Magazine, issue 155, October 2013, pg. 58: http://www.linuxpromagazine.com/Issues/2013/155/Ask-Klaus
