Serving false signatures to attack scanners with Portspoof
Flytrap

The Internet is a tough place to live – especially for publicly accessible computers. A small tool called Portspoof makes port scanning a real challenge for attackers.
Seasoned attackers, and even some amateur cyber-vandals, find sport in trying to scan servers and hijack them at the same time (Figure 1). Firewalls and Intrusion Detection/Prevention systems can help, but if a single tool could truly stop all potential attacks, the Internet intrusion industry wouldn't even exist.
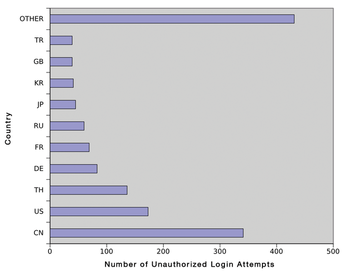
A professional intrusion attempt is typically preceded by reconnaissance and scanning. Many attackers simply perform a scan, which is easily automated with tools like Nmap. An attacker who discovers a firewall and similar defensive system can often guess which ports and services are worth attacking. However, a tool called Portspoof [1] intervenes to cause complications and confusion for the attacker. Portspoof answers port requests with a wild mix of signatures and payloads. This confusing and unwanted information slows down any attempted port scan, forcing the attacker to manually evaluate the results in a time-consuming process.
[...]
Buy this article as PDF
(incl. VAT)