Neatly managing and handling PGP/GnuPG keyrings
Key Service

PGP/GnuPG is becoming increasingly popular, thanks to digital crime and government surveillance. We take a look behind the scenes and show how you can keep your keyring current and valid.
If you want to encrypt your data traffic, you first have to gain a general understanding of the concepts and individual steps necessary. Pretty Good Privacy (PGP) or GNU Privacy Guard (GnuPG) let you create key pairs – public and private – and group your keys in keyrings. In this article, I discuss the tools for managing these keyrings and keeping them up to date, including checking them regularly for validity.
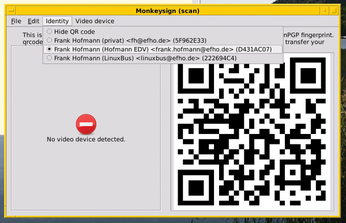
Once you have your key pair, you pass your public key to your communication partners. Traditionally, that either occurs directly as a character string in an email attachment [1], in printed form (e.g., during a key-signing party) [2], or by downloading the key from a web page. For some time, it's been possible to use QR codes that you can receive, check, and manage on your smartphone. In Figure 1, you can see the Monkeysign [3] GUI with the QR code key.
[...]
Buy this article as PDF
(incl. VAT)