(In)secure?
Ubuntu derivative BackBox Linux for security analysis

© Lead Image © Andrea De Martin, 123RF.com
Specializing in security and forensics, BackBox Linux is not only good for a vulnerability assessment, but thanks to its lean substructure, it is also suitable as a desktop distribution.
Many security-related Linux derivatives focus on a specific area of IT security and only take other problems into account marginally, or not at all. In contrast, the Italian Ubuntu derivative BackBox Linux, which has been in continuously development for several years, addresses most of the security-relevant issues faced by administrators of small and medium-sized networks.
You can pick up the approximately 2.5GB ISO image from the BackBox project page [1] for both 32- and 64-bit architectures. Here, you can choose whether you want to download the image directly or via BitTorrent. You can either specify a donation amount or enter 0 in the corresponding field.
As the minimum system requirements, the developers specify a computer with 1GB of RAM and 10GB of free space on mass storage. The screen resolution should be at least 800x600 pixels; both a USB memory stick and a DVD can be used as boot drives.
Much like Ubuntu, the system starts up automatically without intervention on booting. If you press a key in the first five seconds, a selection menu appears in which you can specify the localization, if needed. After a short time, an Xfce v4.11 desktop appears in a conventional design with a horizontal panel at the top of the screen (Figure 1).
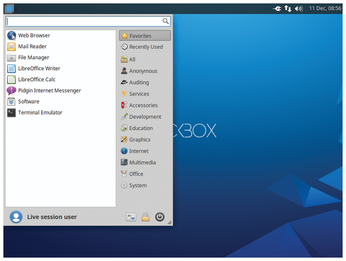
At first glance, three unusual categories stand out in the start menu: the Anonymous, Auditing, and Services submenus indicate the distribution's universal applicability for security-related tasks. On the desktop itself, in addition to the obligatory recycle bin and some icons for existing drives and folders, there is also a launcher to install the system on the mass storage device.
Clicking on the launcher activates Ubiquity, Ubuntu's default installation wizard, which appears in brighter colors on BackBox than on the original Ubuntu.
Software
BackBox Linux is based on Ubuntu 14.04, with kernel 4.4 underpinnings and systemd. The distribution comes with many popular preinstalled programs, including LibreOffice 4.2.8, Firefox 50.0.2, Gimp 2.8.10, and Thunderbird 45.5.1. However, multimedia programs such as VLC and Audacity are missing, and you won't find a Games submenu.
For this purpose, in the Services folder, BackBox offers the option to start or stop various services and processes with a mouse click. These include the Apache web server, the Tor anonymization network, the PostgreSQL database, and the SSH daemon. The status of these services can be easily determined with a mouse click (Figure 2).
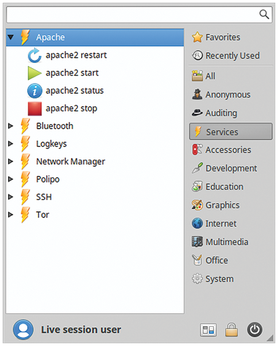
You can use the BleachBit delete tool to remove unnecessary and obsolete data, which mainly includes rotating logfiles, but also temporary storage or histories that show a user's behavior on the computer. BackBox offers two starters: one for users and one for administrators with extended permissions.
In the Anonymous menu, you can start, stop, or determine the current status of the anonymous service by clicking the like-named scripts (e.g., anonymous start). The anonymous script lets you generate an incorrect MAC address for one of the network interfaces integrated into the system. The service also lets you modify the hostname and finally starts the Tor anonymizing service.
The entire script runs interactively in the terminal. To open an Internet connection secured by a Tor network, click on Vidalia in the Internet menu. The graphical Vidalia control panel, which provides a great deal of interesting information about Tor in a visual format, automatically establishes the connection to the service (Figure 3).
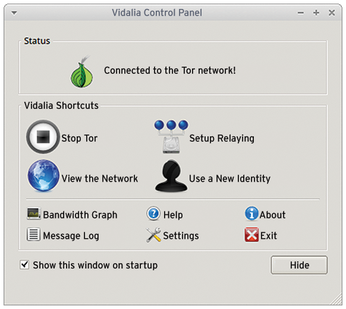
In the Anonymous menu you will also find a launcher that calls a script to erase the memory before switching off. Switch this function on or off in the terminal after entering your authentication data.
Unlike other IT security distributions, BackBox does not provide the Firefox web browser with add-ons by default. You will therefore want to reinstall and configure uBlock Origin, Ghostery, or HTTPS Everywhere to stop unmanageable tracking by advertising agencies.
Pidgin, the preinstalled chat client, optionally supports encrypted communication using the OTR plugin, but you have to install this extension manually. In the Thunderbird email client, I also recommend setting up add-ons such as Enigmail, which allow messages to be simply encrypted with OpenPGP or GnuPG.
Core
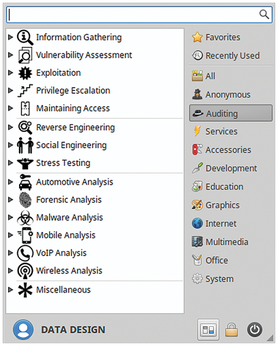
The core of BackBox is the Auditing menu, with 16 groups of security-related applications. In addition to tools for penetration tests, you will also find many programs for network and web app analysis, as well as forensic tasks. It also contains well-known sniffers and vulnerability analysis programs.
The developers also incorporated some unusual tools into the system: For example, tools from the Automotive Analysis submenu can be used to read the CAN bus of motor vehicles, whereas Mobile Analysis deals with smartphones and tablet PCs. The Android and iPhone submenus group the respective applications by system type.
The Wireless Analysis submenu, which distinguishes between Bluetooth and WiFi applications, is similarly laid out. Under WiFi | Cracking, you will find programs for checking WiFi encryption, such as Aircrack-ng. The Scanning submenu combines applications for detecting WiFi networks, including the Kismet program.
Various applications for LAN analysis offer significant benefits: Password crackers, some of which can be used for specific file types, make it possible to trace password strength. With network sniffers such as Ettercap and Wireshark, you can also quickly identify weak points in the intranet by recording data transfer (Figure 4).
In addition to software that exclusively deals with computer and data security, you will find tools for reconstructing data in various subgroups in the Forensic Analysis menu. This includes – especially in the Data Recovery submenu – applications such as PhotoRec, TestDisk, Scalpel, and Foremost. The same menu also has applications for file and partition analysis.
All-Rounder
Thanks to the lean Xfce desktop, BackBox is already very efficient with resources by nature. For example, with its graphical desktop and all commonly started services, the system only occupies about 500MB of RAM, which means that it runs smoothly, even on poorly equipped computers. Because most of the supplied tools start in the terminal, they do not require any additional memory.
Thanks to the low hardware requirements, BackBox is also suitable as a solid all-rounder for daily desktop use. For this reason, the developers implemented the graphical Synaptic front end for package management, which also makes it easy to install updates.
Package management already specifies all package sources, including those from third-party providers and the Tor Project, so you can keep your security-relevant software up to date at all times. Therefore, Synaptic lists more than 48,000 packages for the BackBox system (Figure 5).
Buy this article as PDF
(incl. VAT)
