The Tor Network: Tools for private and secure browsing
Passing Secrets

The Tor project supports a formidable collection of tools for protecting your privacy on the Internet. We'll give you some background on Tor and help you get started with the Tor Browser.
Computer users leave broad trails across the Internet. The websites you visit, your interactions, your purchases, your common passwords if you are careless – everything you do online – can be noted and used against you for purposes that range from the annoying to the dangerous, depending on your circumstances. Fortunately, a growing number of applications exist to restore your privacy and security, and the most mature of these is the Tor Browser [1] (Figure 1).
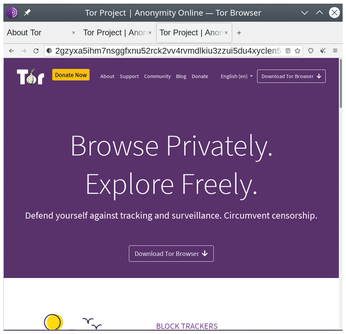
Tor (short for The Onion Router) is a modified version of Firefox designed to hide your trails on the Internet. Tor obscures your electronic trail by routing your interactions through several servers and encrypting your actions each step of the way. Tor's network of servers is decentralized, making your communications even harder to track down. Over the last two decades, several features have been added to the basic browser, providing a defense in depth against privacy and security intruders.
[...]
Buy this article as PDF
(incl. VAT)