Simplify your firewall setup
Fine Tuning
Ufw stores all the rules and enables them automatically after a system reboot. The IPv4 rules are stored in the /etc/ufw/user.rules file, and the IPv6 counterparts in /etc/ufw/user6.rules. After creating new rules, you should reload these files for safety purposes by typing:
sudo ufw reload
Based on the default rules, ufw allows all outgoing connections. To specifically deny a service access to the network, use deny instead of allow. In addition, use out at the end of the line to indicate that the rule applies to outgoing connections. For example, to prohibit outgoing traffic on port 22, use:
sudo ufw deny out ssh
After issuing this command, the system can no longer contact another host via SSH. Rules for incoming connections are tagged in the same way with in. In all the previous examples where this keyword is missing, ufw automatically assumes that the rule applies to incoming connections.
In addition to allow and deny, reject signifies that the firewall does not simply ignore access attempts but also notifies the sender of the attempts. Also, comment lets you attach a note to all rules (Listing 2, first line). Each rule always applies to all network interfaces. To restrict a rule to one interface, specify its name after in or out (Listing 2, second line).
Listing 2
Comments and Interfaces
$ sudo ufw reject out ssh comment 'no ssh access allowed' $ sudo ufw allow in on enp0s3 ssh
Bouncer
Access via SSH should only be allowed for defined hosts. To do this, first deny SSH access globally with
sudo ufw deny ssh
Since this is also the default setting, you can alternatively remove the rule
sudo ufw delete allow ssh
which deletes the allow ssh rule. If you can't remember the rules, call
sudo ufw status verbose
In addition, each rule is internally given a sequential number, which can be displayed with:
sudo ufw status numbered
You can use these numbers to delete specific rules. For example, to remove the rule assigned the number 2, use:
sudo ufw delete 2
Now that access via SSH is generally blocked, the command shown in Listing 3 exclusively allows SSH access for the computer with the IP address 192.168.1.101. If you omit to any port 22, the IP address is allowed to access all services. Similarly, you can use deny to block specific requests from an IP address.
Listing 3
Unblocking
$ sudo ufw allow from 192.168.1.101 to any port 22
Numerous requests within a short time indicate an attack and can also overload the affected service. If so desired, ufw can detect this kind of access attempt and then block it specifically. Currently, however, this useful function only works with IPv4 connections. For example, the firewall monitors the SSH service with the command
sudo ufw limit ssh
and blocks access if there are too many requests in a short time.
Chatterbox
If you get tangled up in too many rules, use the following command to start over:
sudo ufw reset
When creating new rules, you can use various reports for help. Use
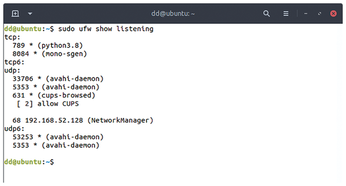
sudo ufw show listening
to return all services that are currently listening on any port. This helps you find applications that you didn't know were running or that shouldn't be running at all (Figure 3).
If you are familiar with iptables, you can take an in-depth look into the firewall's current configuration with:
sudo ufw show raw
Ufw stores detailed information about its work in a log, which you can enable with
sudo ufw logging on
and then view in /var/log/ufw.log.
« Previous 1 2 3 Next »
Buy this article as PDF
(incl. VAT)
Buy Linux Magazine
Subscribe to our Linux Newsletters
Find Linux and Open Source Jobs
Subscribe to our ADMIN Newsletters
Support Our Work
Linux Magazine content is made possible with support from readers like you. Please consider contributing when you’ve found an article to be beneficial.

News
-
So Long Neofetch and Thanks for the Info
Today is a day that every Linux user who enjoys bragging about their system(s) will mourn, as Neofetch has come to an end.
-
Ubuntu 24.04 Comes with a “Flaw"
If you're thinking you might want to upgrade from your current Ubuntu release to the latest, there's something you might want to consider before doing so.
-
Canonical Releases Ubuntu 24.04
After a brief pause because of the XZ vulnerability, Ubuntu 24.04 is now available for install.
-
Linux Servers Targeted by Akira Ransomware
A group of bad actors who have already extorted $42 million have their sights set on the Linux platform.
-
TUXEDO Computers Unveils Linux Laptop Featuring AMD Ryzen CPU
This latest release is the first laptop to include the new CPU from Ryzen and Linux preinstalled.
-
XZ Gets the All-Clear
The back door xz vulnerability has been officially reverted for Fedora 40 and versions 38 and 39 were never affected.
-
Canonical Collaborates with Qualcomm on New Venture
This new joint effort is geared toward bringing Ubuntu and Ubuntu Core to Qualcomm-powered devices.
-
Kodi 21.0 Open-Source Entertainment Hub Released
After a year of development, the award-winning Kodi cross-platform, media center software is now available with many new additions and improvements.
-
Linux Usage Increases in Two Key Areas
If market share is your thing, you'll be happy to know that Linux is on the rise in two areas that, if they keep climbing, could have serious meaning for Linux's future.
-
Vulnerability Discovered in xz Libraries
An urgent alert for Fedora 40 has been posted and users should pay attention.

