Programming Snapshot – Pushover
The Bouncer

© Lead image, Vlad Kochelaevskiy, 123RF
A number of sensors and cameras send author Mike Schilli a short message if someone tampers with his apartment door. He has now applied this security principle to the SSH entrance of his Linux computer.
As an alternative to the Prowl solution for sending text messages described in a previous article [1], another provider in the colorful world of phone apps, Pushover, now – for a one-off payment of $5 – lets you distribute 7,500 messages a month for the rest of your life through a web API to either iOS, Android, or desktop clients.
Rough and Ready Browser
On iOS or Android, the user logs in to the Pushover app, which then displays incoming messages as push notifications (Figure 1), even if the phone isn't being used and displays the lock screen. Additionally, Pushover offers native desktop clients for the Mac and a somewhat hacky browser solution for the Linux desktop.
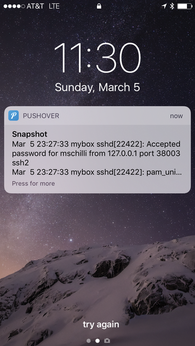
[...]
Buy this article as PDF
(incl. VAT)