Kaspersky Analysis: Black Market in Botnets
Virus analyst Yury Namestnikov investigated the structure, functionality and business model of botnets for antivirus firm Kaspersky Lab with some surprising results.
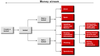
Since the time decades ago when networks consisted of a few dozen centrally controlled computers, botnets have steadily increased in number. Kasperky's Namestnikov speaks of the current widely distributed systems of millions of hijackable systems with decentralized control. The reason behind these zombie networks, as he calls them, is the money to be made, and that with little technical know-how.
Getting on board the cybercrime business no longer requires you to be a programmer. Cybercrime forums are now easily available on the Web to help in creating zombie networks and infecting them with netbots. "Bots for sale" signs are everywhere. And to make it even more egregious, obfuscation and encryption can also be applied to the bot code to keep it from being detected.
A netbot generator next has to work for its distribution, per spam, forum and social network postings or drive-by downloads. Bots often include self-replication functions that act as viruses or worms.
The tricks cybercriminals employ are often quite simple. One is drive-by downloads. Before downloading an interesting video, a user might first need to install a special program. When the user visits a prepared website, the drive-by download exploits a security hole in the browser to download malware, without the user suspecting a thing.
Income for cybercriminals can come from distributed denial-of-service (DDoS) attacks, theft of confidential information, spams, phishing, search engine spamming, click fraud and distribution of adware and malicious programs. As Namestnikov notes in his analysis, "if chosen, any of these sources can provide a cybercriminal with a good income. But why choose? A botnet can perform all of these activities- at the same time!"
| Gallery (3 images) |
|---|
|