Resetting Passwords with SystemRescueCd
SystemRescueCd
ByIf you’re locked out of your Linux or Windows system, a handy Live Linux troubleshooting distro might be all you need to get back in. We’ll show you how to pick the lock with SystemRescueCd.
Getting locked out of your Linux or Windows system is a frustrating experience. These days, not being able to log in to your system might be worse than getting locked out of your car; at least with a car you can get a ride home or contact a locksmith to get back in. However, if you’re locked out of your Linux system, you’re really not going to find a competent ready-made service to come to your rescue.
But never fear: The open source community offers some powerful tools for helping you reset passwords. For instance, the GRUB and LILO boot managers offer some recovery options. If you need something more versatile, the SystemRescueCd disk project provides a number of tools for resetting passwords and recovering your system. SystemRescueCd doesn’t just reset passwords in your Ubuntu, Red Hat, or Linux Mint system: It can also help you recover access to your Windows computer.
GRUB’s System Recovery Mode
Sometimes you don’t need a specialized tool like SystemRescueCd to get back on your system. The traditional Unix/Linux single-user mode might be all you need. If your system uses the GRUB bootloader, you can enter Linux single mode through GRUB’s Recovery Mode and boot menu options. (An equivalent process is also available for the LILO bootloader; see the box titled “Using LILO.”)

Recovery Mode is available to you no matter what Linux flavor you are using (e.g., Ubuntu 12.04 “Precise Pangolin,” Red Hat Enterprise Linux 6, Fedora 16, or Linux Mint 12).
When using GRUB to enter Linux single-user mode, first, make sure you have removed any and all external drives or connections. More than once, I’ve confused the issue by trying to mount external USB drives and other devices when I was working to recover my primary hard disk.
When you’re sure you’ve stripped things down to the bare bones, boot your system so the GRUB menu is showing and choose the kernel into which you want to boot. Usually, you will boot into the first kernel listed on the menu, but you can make sure you’re booting into the latest version by reading the numbers – the higher the number, the more current. You can choose the kernel by simply hitting the Up or Down arrow key.
Once you’ve selected the kernel version, press the e key to edit the entry. In the simple text editor, choose the line starting with the word kernel (usually the second line on your screen). After selecting the kernel line, press the e key to edit the kernel entry. Append the following to the end of the kernel line:
S
Yes, just use the letter S, without quotes. You can also use the word Single without quotes.
When you press Enter, you will exit the editor and be placed back at the GRUB menu. The menu will now have the modified kernel line (e.g., the line with the capital S at the end).
To boot into Linux single-user mode, press the b key. You’ll know you’ve entered Linux single-user mode once you see a simple root prompt, denoted by the hash mark (#). You won’t see any other information on the prompt as you normally would (e.g., the username, system name, or current directory).

Usually, you can simply reset the password using the passwd command at this point (see the “Warning: Don’t Misuse This Information” box). However, depending on how your system is configured, you might need to mount some partitions: /proc/, /var/, or the root directory itself (/):
# mount -t proc proc /proc # mount -o remount,rw /
Once you’re at the prompt, enter
passwd
and press Enter. You will be prompted to enter a new password, so go ahead and do so and press Enter to confirm your choice. Next, you can reboot the system with the reboot command, log in to the root account, and change any other passwords as necessary.
Rescuing with SystemRescueCd
SystemRescueCd is a Live Linux distribution similar to Knoppix. The distribution is designed for system troubleshooting, which means it lets you:
- change user passwords in Linux or Windows systems, including the passwords for the root and Administrator accounts;
- check the integrity of existing partitions;
- create new partitions or format existing partitions using the parted tool or the graphical equivalent, GParted (Figure 1); and
- recover files from unbootable Linux or Windows systems.
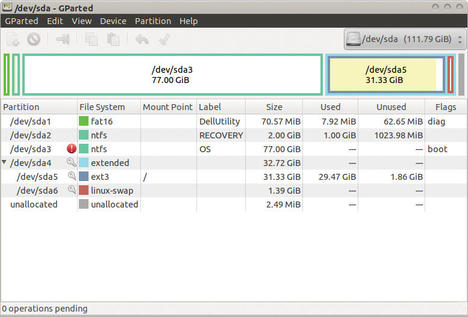
Of course, most of the troubleshooting tools found on SystemRescueCd are available for other Linux distributions as well.
The basic procedures described in this article will work with other Live Linux troubleshooting distros, although the details might vary. In this case, I’m using SystemRescueCd as an example of how to reset passwords by booting the system from a Linux Live disk.

I should add that SystemRescueCd uses the Zsh command shell by default, which could be confusing for users who are accustomed to the Bash shell. Every once in a while when using SystemRescueCd, I get a funky error message that tells me I am using the wrong shell.
If you are not familiar with Zsh and would prefer to work in Bash, you can easily change the shell from Zsh to Bash by entering the following export command:
export SHELL=/bin/bash
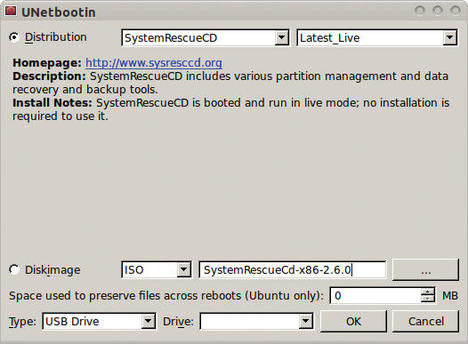
Once you’ve downloaded the SystemRescueCd image from the project website, you can use any appropriate tool to burn the image to a CD or a Flash drive. See the “Using UNetbootin” sidebar for more on burning the image to a USB stick.
Resetting Passwords
Sometimes your system is damaged in a way that won’t let you reset the password using Linux single-user mode. To reset a Linux-based password in SystemRescueCd, start by booting to the SystemRescueCd Live system.
To find out which disk partition contains the /etc directory, use fdisk. The /etc partition is usually on the root (/) drive. See the command and output in Listing 1.
Listing 1: Listing Partitions with fdisk
01 #fdisk -l Device Boot Start End Blocks Id System /dev/sda1 63 144584 72261 de Dell Utility /dev/sda2 145408 4339711 2097152 7 HPFS/NTFS/exFAT /dev/sda3 * 4339712 165822455 80741372 7 HPFS/NTFS/exFAT /dev/sda4 165822930 234436544 34306807+ 5 Extended /dev/sda5 165822993 231528779 32852893+ 83 Linux /dev/sda6 231528843 234436544 1453851 82 Linux swap / Solaris
In Listing 1, the /dev/sda5 directory is the main partition, as revealed by its size and partition type, so you will need to mount this partition. To do so, first create a directory that will act as a mountpoint:
mkdir /mnt/bootdir
Now, mount the Linux partition to your SystemRescueCd partition:
mount /dev/sda5 /mnt/bootdir
The chroot command lets you access it easily:
chroot /mnt/system
Now, you can reset your password using the passwd command,
passwd <newpassword>
where newpassword is the new password you want to use.
The umount command unmounts the partition, after which you can reboot. Once you log back in to your troubled Linux system, you’ll be able to use the root account with the new password you’ve specified.
Mounting Disks
Once you have accessed the system with SystemRescueCd, you don’t have to go stampeding to the passwd command and then rush out again. If necessary, you can mount drives and edit key files. In fact, once you enter Linux single-user mode, you can edit and browse through directories or make changes to critical text files.
For example, instead of using the passwd command, you could edit the /etc/shadow file directly and remove the password information. To do this, mount the partition that contains the /etc directory – this is usually the root partition – and enter the command:
# mount -rw / /mnt/partition
If necessary, create the /mnt/partition directory. Once you’ve mounted the / partition, simply use vi, Emacs, or another text editor to access the /etc/shadow file and edit the file so that the user account of your choice (e.g., the root account) no longer contains the hashed password information. Then, unmount this partition, reboot, and access your Linux system in a standard session. At this point, you’ll be able to log in to the account without specifying a password.
Resetting GRUB Boot Password Protection
But, you ask, what if you have password-protected GRUB and have forgotten that password? Isn’t it impossible to get past this password to enter single-user mode? With SystemRescueCd, you can mount the /boot partition, or the root (/) partition, as discussed above.
To begin, switch to the /boot/grub/ directory and copy the unedited file to the same directory under a new name:
cp /boot/grub/menu.lst /boot/grub/menu.lst_bak
This is an important step, just in case you edit the file incorrectly. In a text editor, edit the /boot/grub/menu.lst file and look for the following line:
password -md5 $1$gLhU0/$aW78kHK1QfV3P2b2znUoe/
Now, comment out the password entry and save your changes. Then, unmount the directory and reboot your system. Once you’ve taken these steps, you’ll be able to bypass the GRUB password.
Resetting Passwords on a Windows System
You can use the tools on your disk to boot into a Windows partition as well. Suppose you want to boot into Windows and change the password for a user account.
To begin, boot into SystemRescueCd and using fdisk to list existing partitions like this:
fdisk -l
Next, look for an NTFS partition that appears to be the Windows system partition. For example, you might see a line that reads:
/dev/sda3 (NTFS)
Once you have found the correct NTFS drive (I’ll assume it is /dev/sda3), use the ntfs command:
ntfs -3g /dev/sda3 /mnt/windows -o force
This command mounts the NTFS drive on /dev/sda3 onto your local /mnt/windows/ drive. If this drive isn’t available, create it as follows:
mkdir /mnt/windows
Once you’ve mounted the NTFS drive onto the /mnt/windows/ drive, change to it:
cd /mnt/windows/Windows/System32/config
Now, you are ready to use the chntpw command to list the Windows accounts in the SAM database:
chntpw -l SAM
The result of the preceding command will be a list of user account names.
Next, you can select the account name that requires a password reset. In this case, I’ll assume you want to change the account of a user named James Stanger:
chntpw -u "James Stanger"
Once you issue the above command, you will see a menu of various options. To reset the password, press 1 and Enter. You will be asked to confirm that you want to reset this account, so press the y key and Enter. The account is now reset.
To reboot, enter the reboot command and press Enter. You’ll find you can get into your account (e.g., James Stanger) without entering a password.
SystemRescueCd makes it pretty easy. The preceding steps will simply change the password. If you want to get full read-write access to a Windows disk, you can enter the command
ntfs-3g /dev/sda1 /mnt/windows
and then you’ll be able to mount the disk and copy or even write files to it. I would recommend, however, simply copying files from your Windows system; writing to another filesystem is always fairly risky, especially one that isn’t based on Linux. Once you have mounted your Windows drive, you can then simply navigate through it using the cd command as you would a Linux system – more or less.
Conclusion
Now you know how to give your system passwords the boot. Although you might be able to reset your passwords in Linux single-user mode, accessed through the GRUB (or LILO) bootloader, SystemRescueCd offers another, more versatile alternative.
I suppose it’s worth reiterating here that you’re not supposed to use these tools for malicious purposes. And by “malicious,” I mean you’re not supposed to use these tools to break into someone else’s system or view information and data that isn’t meant for you. If I need to spell this out further, I suggest you get out of “techie mode” for a bit and take a good ethics class. At any rate, SystemRescueCd is a powerful tool. Enjoy using it responsibly!
Info
[1] UNetbootin
Subscribe to our Linux Newsletters
Find Linux and Open Source Jobs
Subscribe to our ADMIN Newsletters
Support Our Work
Linux Magazine content is made possible with support from readers like you. Please consider contributing when you’ve found an article to be beneficial.

News
-
Chaos Comes to KDE in KaOS
KaOS devs are making a major change to the distribution, and it all comes down to one system.
-
New Linux Botnet Discovered
The SSHStalker botnet uses IRC C2 to control systems via legacy Linux kernel exploits.
-
The Next Linux Kernel Turns 7.0
Linus Torvalds has announced that after Linux kernel 6.19, we'll finally reach the 7.0 iteration stage.
-
Linux From Scratch Drops SysVinit Support
LFS will no longer support SysVinit.
-
LibreOffice 26.2 Now Available
With new features, improvements, and bug fixes, LibreOffice 26.2 delivers a modern, polished office suite without compromise.
-
Linux Kernel Project Releases Project Continuity Document
What happens to Linux when there's no Linus? It's a question many of us have asked over the years, and it seems it's also on the minds of the Linux kernel project.
-
Mecha Systems Introduces Linux Handheld
Mecha Systems has revealed its Mecha Comet, a new handheld computer powered by – you guessed it – Linux.
-
MX Linux 25.1 Features Dual Init System ISO
The latest release of MX Linux caters to lovers of two different init systems and even offers instructions on how to transition.
-
Photoshop on Linux?
A developer has patched Wine so that it'll run specific versions of Photoshop that depend on Adobe Creative Cloud.
-
Linux Mint 22.3 Now Available with New Tools
Linux Mint 22.3 has been released with a pair of new tools for system admins and some pretty cool new features.
