Features
Building Frames
Building Frames
FFmpeg is good not only for converting and fusing videos together, it can also generate streams on the fly, which you can then use for compositing and effects.
Meticulous Transformer
How compilers work
Compilers translate source code into executable programs and libraries. Inside modern compiler suites, a multistage process analyzes the source code, points out errors, generates intermediate code and tables, rearranges a large amount of data, and adapts the code to the target processor.
DisplayCAL
Color Coordinated with DisplayCAL
If you work with digital images, you know the colors on your monitor don't always match what you see in real life. If you're looking for a more accurate representation of color, try calibrating and profiling your monitor using a colorimeter and DisplayCAL.
Simplifying SSH
EasySSH lives up to its name and starts SSH connections at the click of a mouse.
Saving Your Analog Data from Oblivion
If you have old VHS tapes or audio cassettes lying around, the hardware to play these analog formats is becoming more difficult to find. Here's how to convert those old analog treasures to digital format for future enjoyment.
Paint by Numbers
Design your own boot menu with Grub Customizer
Is the simple black and white GRUB menu causing confusion and obscuring important choices? Why not customize with GRUB themes and the Grub Customizer?
Close to Your Heart
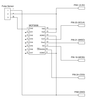
Build your own pulsemeter
A pulsemeter built with a Raspberry Pi, a digital-to-analog converter, and an optical sensor monitors your heart rate just as well as many far more expensive medical devices.
Key Keeper
Data Security in the AWS Cloud
As a cloud market leader, Amazon Web Services has had to put a great deal of thought into data security. Encryption options and key management play an important role.
Tutorial – LÖVE animation
A LÖVE animation primer
LÖVE is an extension of the Lua language, designed to make developing games easy. In this tutorial, we'll explore this framework by creating some animated sprites.
Sync or Swim
Synchronize your data across multiple devices with Syncthing
If you need a cloudless solution for syncing data across multiple devices, Syncthing could be just the thing.
Subscribe to our Linux Newsletters
Find Linux and Open Source Jobs
Subscribe to our ADMIN Newsletters
Support Our Work
Linux Magazine content is made possible with support from readers like you. Please consider contributing when you’ve found an article to be beneficial.

News
-
Nitrux 6.0 Now Ready to Rock Your World
The latest iteration of the Debian-based distribution includes all kinds of newness.
-
Linux Foundation Reports that Open Source Delivers Better ROI
In a report that may surprise no one in the Linux community, the Linux Foundation found that businesses are finding a 5X return on investment with open source software.
-
Keep Android Open
Google has announced that, soon, anyone looking to develop Android apps will have to first register centrally with Google.
-
Kernel 7.0 Now in Testing
Linus Torvalds has announced the first Release Candidate (RC) for the 7.x kernel is available for those who want to test it.
-
Introducing matrixOS, an Immutable Gentoo-Based Linux Distro
It was only a matter of time before a developer decided one of the most challenging Linux distributions needed to be immutable.
-
Chaos Comes to KDE in KaOS
KaOS devs are making a major change to the distribution, and it all comes down to one system.
-
New Linux Botnet Discovered
The SSHStalker botnet uses IRC C2 to control systems via legacy Linux kernel exploits.
-
The Next Linux Kernel Turns 7.0
Linus Torvalds has announced that after Linux kernel 6.19, we'll finally reach the 7.0 iteration stage.
-
Linux From Scratch Drops SysVinit Support
LFS will no longer support SysVinit.
-
LibreOffice 26.2 Now Available
With new features, improvements, and bug fixes, LibreOffice 26.2 delivers a modern, polished office suite without compromise.