This trusty troubleshooting tool can track processes along with network traffic
Quick Results
One of the concerns often voiced online about Ptcpdump relates to performance. Because the tool requires more information from the running system to assemble its output than was the case with its older predecessor, the process takes longer. On top of this, the program has to correlate this data for each line it displays.
In practical terms, though, this has virtually no effect on the speed. If you don't have any problems with Tcpdump on your system, you won't have any with Ptcpdump either. All the output takes place in real time; the tool does not trip over its toes if it has to write a flood of data on the command line. Like its predecessor, it even lets you pipe the collected information directly to an instance of Tshark or Wireshark, which means you can inspect the data in close to real time.
Compatible, But ?
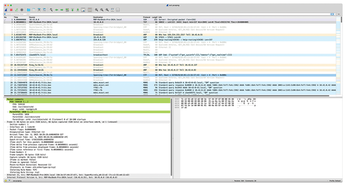
Ptcpdump is based on the amazing eBPF and offers many functions that Tcpdump does not support or cannot implement. But even in this universe, not all that glitters is gold. For admins who are used to working with Tcpdump and Wireshark, the current lack of compatibility of Pcap output is a kind of a showstopper. TCPdump provides no PID information, which means it won't work easily with Wireshark. Ptcpdump correctly extends its Pcap files in PCAP-NG format [5] to provide the fields required for Wireshark support, but Wireshark can't evaluate the information dynamically and display the matching processes live in the output (Figure 5). You need to work with a mix of several tools and call on old acquaintances such as Htop or ps fauxw to correlate the data.
Outlook
All told, Ptcpdump is a largely CLI-compatible alternative to its popular ancestor Tcpdump. In most cases, you can install Ptcpdump locally and then reference it using an alias. The fact that the installation is currently still a slightly rough ride is mainly due to the fact that packages are still unavailable for many popular Linux distributions. Installing directly from the project's GitHub page does not cause any problems, however, administrators who are confronted with monitored systems and compliance requirements in production settings will want to avoid the GitHub option.
GitHub already has a bug report for Debian GNU/Linux that highlights the need for a Debian package. As soon as such a package exists, Ptcpdump will also find its way into Ubuntu. The situation is less clear for Suse, Red Hat, and other alternatives. One reason for the slow adoption is that you actually have to install Ptcpdump directly on the affected system; you can't simply roll it out in a container. Admins can only hope that, as Ptcpdump continues to spread, more Linux developers will take an interest in integrating it into their platforms. As soon as the tool makes its way into the popular distributions, its fan base is likely to expand.
Infos
- Tcpdump: https://www.tcpdump.org
- Pcap: https://www.tcpdump.org/pcap.html
- Ptcpdump: https://github.com/mozillazg/ptcpdump
- Skbdump: https://github.com/jschwinger233/skbdump
- PCAP Next Generation: https://wiki.wireshark.org/Development/PcapNg
« Previous 1 2
Buy this article as PDF
(incl. VAT)
Buy Linux Magazine
Subscribe to our Linux Newsletters
Find Linux and Open Source Jobs
Subscribe to our ADMIN Newsletters
Support Our Work
Linux Magazine content is made possible with support from readers like you. Please consider contributing when you’ve found an article to be beneficial.

News
-
KDE Linux Alpha Available for Daring Users
It's official, KDE Linux has arrived, but it's not quite ready for prime time.
-
AMD Initiates Graphics Driver Updates for Linux Kernel 6.18
This new AMD update focuses on power management, display handling, and hardware support for Radeon GPUs.
-
AerynOS Alpha Release Available
With a choice of several desktop environments, AerynOS 2025.08 is almost ready to be your next operating system.
-
AUR Repository Still Under DDoS Attack
Arch User Repository continues to be under a DDoS attack that has been going on for more than two weeks.
-
RingReaper Malware Poses Danger to Linux Systems
A new kind of malware exploits modern Linux kernels for I/O operations.
-
Happy Birthday, Linux
On August 25, Linux officially turns 34.
-
VirtualBox 7.2 Has Arrived
With early support for Linux kernel 6.17 and other new additions, VirtualBox 7.2 is a must-update for users.
-
Linux Mint 22.2 Beta Available for Testing
Some interesting new additions and improvements are coming to Linux Mint. Check out the Linux Mint 22.2 Beta to give it a test run.
-
Debian 13.0 Officially Released
After two years of development, the latest iteration of Debian is now available with plenty of under-the-hood improvements.
-
Upcoming Changes for MXLinux
MXLinux 25 has plenty in store to please all types of users.


