Android Admin Tools
Linux Remote Administration on Android and iOS
BySmartphones and tablets have lost their gadget status and become part of the system administrator’s tool kit. We look at the most important apps for admins.
In the pre-smartphone era, which was not so long ago, it was hard to imagine a practical use for a mobile device in system administration – if you discount laptops with graphical and web interfaces or terminal software designed for high latency.
All that has changed: With ubiquitous broadband and mobile data connections and with hotspots and WLANs widespread in the enterprise, admins are increasingly able to leave their desks and get out of the server room. Smartphones and tablets with sufficiently large screen sizes are mutating into multifunctional tools that can do most of the important tasks while on the road or in an emergency.
Device Zoo
Android devices are not characterized by any kind of version homogeneity, so we decided to test the programs on various devices: a Nexus 4 with the latest Android 4.3, a Nook HD+ with a slightly older version of Android 4, an ancient Motorola Defy with Cyanogen Mod 7 Android 2.3.7, a Sony Experia with Android 2.3 and many backports by the manufacturer, and an HTC Desire Z with Android AOSP 4.2.2. None of the tested programs had compatibility issues on any of the devices.
On the Apple front, we had access to an iPhone with iOS 6 and a first-generation iPad with iOS 5 – again, with no compatibility issues (Figures 1 and 2).


Stores and VPN
If you rummage through the Google Play Store or Apple’s App Store, you are likely to find a large number of mostly free apps that help sys admins manage the systems they support in a reasonably convenient way while using a fairly small mobile device. Additionally, a variety of tools sprinkled throughout the web make life easier for IT professionals.
Most systems are not exposed to the Internet without protection but are, instead, well hidden behind a firewall, so access can only be made via a VPN connection in most cases. Setting up this connection is described for Android and iOS elsewhere.
Lord of the Console
If you frequently manage Unix and Linux servers, your primary tool is going to be an SSH client. On Android devices, ConnectBot by Kenny Root and Jeffrey Sharkey is probably the best choice at this time (Figure 3).
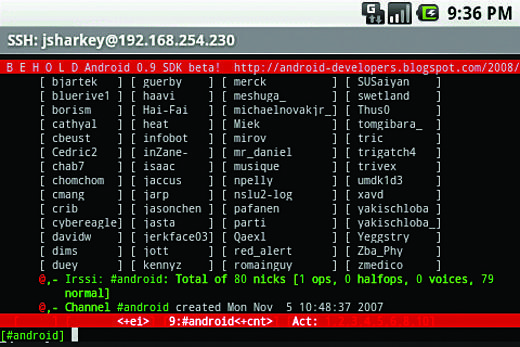
It supports logins using SSH key pairs and can also tunnel ports, which proves especially useful if you want SSH access to replace a full-fledged VPN.
ConnectBot establishes several simultaneous sessions and enables copy and paste to other applications – for example, to inform colleagues of the current system status by mail or to use a cheat sheet with frequently used commands. Even those who use a password manager like KeePassDroid on the road will soon appreciate this function. A nice detail is that ConnectBot can issue commands automatically for the user after login. This post-login automation then takes care of standard tasks such as checking active logins or resources.
X for Android
Executing commands on startup is also useful for exporting a display, so you can start graphical applications in combination with the X Server for Android. Unfortunately, android-xserver does not support the necessary extensions to launch Firefox, for example. Nevertheless, it continues to offer the most comprehensive X server implementation on Android.
Hacker’s Keyboard
If you are familiar with the advantages of keyboard-based controls in a shell, you will definitely appreciate some advanced features for touchscreens, including the often missing Tab key for auto-completion. Only a few Android devices have this practical detail preinstalled (Figure 2), and Hacker’s Keyboard (Figure 4) makes the Unix shell with ConnectBot far more pleasant to use by retrofitting Tab, Ctrl, Esc, and arrow keys.
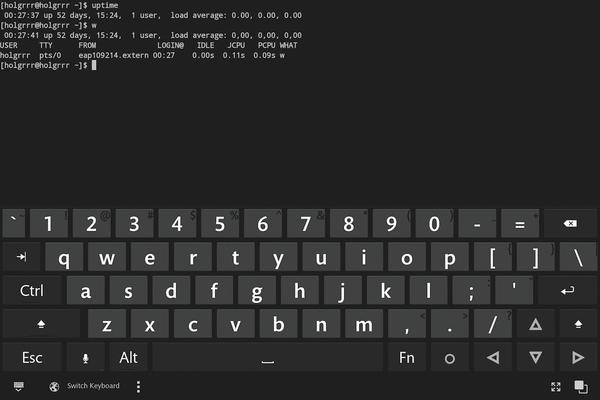
During installation, note that new Android keyboards are not automatically active for safety reasons; instead, the user needs to activate them in the system settings. Although this seems unnecessarily complicated at first, it actually makes perfect sense: Unintentionally installed keyboards could act as keyloggers and sniff passwords, among other things.
Apple Console
On the iOS front, iSSH (Figure 5) provides a powerful SSH client.
Apart from the features described for ConnectBot, it even supports Remote Desktop Protocol (RDP) and Virtual Network Computing (VNC) out of the box, and it comes with its own X server.
You can launch Firefox without any problems, although you do have to make some compromises compared with the mobile version, which is optimized for tablets and smartphones. It’s still better to use a slow Firefox tunneled over SSH than to expose intranet resources.
Thanks to its own X server, iSSH is much more convenient to use than teaming up ConnectBot and an X server because much less configuration effort is necessary.
Remote Windows
If command-line access is not enough, and you also need access to Windows systems, individual apps for terminal server protocols such as RDP and VNC offer a wide selection. This desire for more convenience leads to an app with the cumbersome name PocketCloud Remote RDP/VNC by Wyse Technology, which allows RDP and VNC access to Windows, Linux, and Mac systems and is available for both Android and iOS.
The app supports two ways of logging in. The first asks for the IP address or hostname of the target system, the destination port, and any other necessary login information. The second method, automatic mode, requires PocketCloud Companion to be installed on the target system and a Gmail account. This alternative is especially interesting for private systems regularly monitored beyond the corporate network.
The major restriction with the free version is that it only lets you store one connection. Before creating a new connection, the user must delete the existing one. If this is not enough for you, you can purchase the commercial version for about US$ 15; the Pro version has no such limitations and even includes 256-bit NLA/TLS encryption for RDP connections and support for VMware View.
If you often need to open several different RDP sessions, you can use 2X Client RDP/Remote Desktop. It works even with the ancient Android version 1.6 and allows you to create multiple connections. For VNC access only, Mocha VNC Lite provides an alternative for Android and iOS. Unfortunately, it also allows only one server.
NoMachine
Admins who depend on managing their remote systems on Free NX or the proprietary NX by NoMachine are left out in the cold. Currently, not a single client runs on Android or iOS, although a how-to for geeks describes how to run NX in a chroot environment with Ubuntu on Android; however, the benefits of this solution in the daily grind would appear to be minimal.
NoMachine is apparently working on a client for Android and iOS, but it was not available before we went to print, although it is scheduled to debut December 2013, according to the notice on the download page. The website does not indicate whether versions older than V4 of the protocol are supported. The formerly Italian, now Luxembourg-based, manufacturers have taken some time with the recently released fourth edition of the program – many years in fact, much to the dismay of customers. Patience seems called for.
TeamViewer with Remote Touch
The popular proprietary, but free for personal use, desktop sharing software TeamViewer (Figure 6) is available for the most common desktop operating systems – Windows, Mac OS, and Linux – as well as in a client version for Android and iOS.
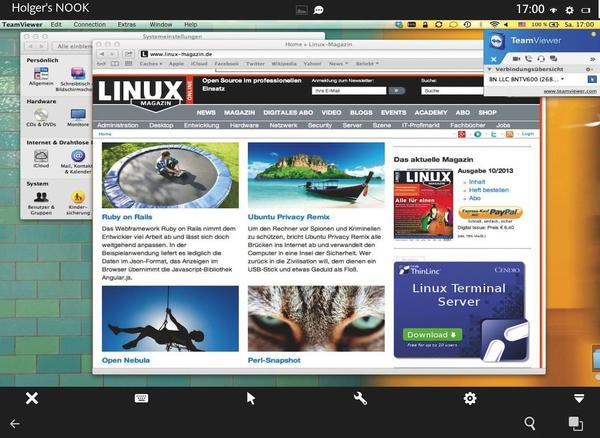
TeamViewer can be used for online presentations or meetings, but is also suitable for remote maintenance tasks. A positive effect to notice here is the Quick Support version that requires no installation and is therefore particularly suitable for spontaneous and uncomplicated support of less technical users.
The users only need to download a program and run it. The software then displays a session ID and a password. If need be, users can pass both of these on to the mobile helper on the phone, which then connects to the system and solves the problem. The remote helper then takes over the helm and can even manage the system via gesture control and handle file transfers in both directions.
Handcrafted
As elegant as a console or a graphical login session can be, a system administrator often just needs answers to the usual questions. How full are the file systems, how many users are logged on to the system, and how long has it actually been running?
If you have not organized your systems in a comprehensive monitoring system like Nagios, you might well appreciate a tool such as Cura-SysAdmin (Figure 7), which is only available for Android.

Cura answers these and other questions and also includes a rather rudimentary terminal emulator, the Nmap port scanner, and a logfile viewer, providing pre-configured access to the main system logs in /var/log, which you can even store on the Android device.
An inelegant, optional feature of Cura prevents installation on Android devices that do not have a SIM card. Cura implements an option for remotely deleting the Cura database and for sending text/email messages with the current positional data in case of loss; thus, GSM connectivity is imperative.
Managing Files with ES File Explorer
Users looking for a file manager that is also suitable for use on a network will inevitably end up knocking at the door of ES File Explorer. Besides its functionality as an easy-to-use file manager with support for ZIP and RAR archives, it offers an integrated file viewer that can handle most formats, and a search function to help you find all files of a certain type on the device, for example.
In the world beyond your own, device-wide protocol support becomes very important. ES File Explorer supports access via FTP, SFTP, FTPS, WebDAV, and CIFS. If you store your data in the cloud, you can open a connection to Dropbox, SkyDrive, GDrive, and Amazon S3, among others. In heterogeneous environments, in particular, it would be delightful to have an implementation of the Network File System (NFS) and the Apple Filing Protocol (AFP), but that is rare on mobile devices.
iOS users who want to access network shares and cloud resources turn to tools such as the commercial FileExplorer, whose free version (FileExplorer Free) remains limited to one target.
Scanning and Sniffing Your Network
Once you have had enough mobile management and want to check out your own network, the versatile Fing (Figure 8) is good for starters.
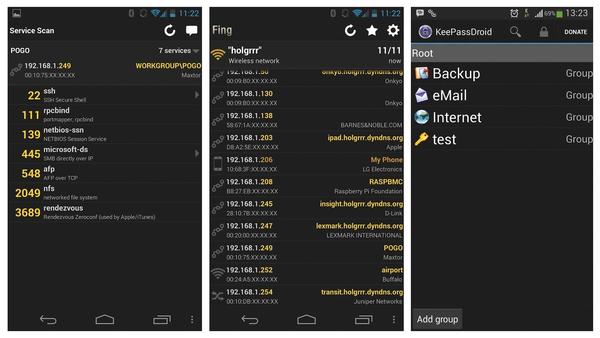
It works on both Android and iOS and scans all the devices registered on the network, revealing the hostname, IP and MAC addresses, and, if possible, the manufacturer of the network device. The concise list can help you quickly determine the IP address of a forgotten device or check to see whether a machine is online and then discover which DHCP address it was assigned by the server. The lists can be stored either on the device or in the manufacturer’s cloud, Fingbox, which is a commercial operation.
Tapping an entry starts a port scan on the corresponding target. If you find open services, you can run the appropriate apps for the service right away. The app suggests ConnectBot for SSH and AndFTP for SCP and SFTP. Also, direct access to CIFS connections via AndSMB is preconfigured, as is access to any web interfaces you discover.
Additionally, you can run a number of classic network tools (e.g., Telnet, Ping, and Traceroute) against a host. The ability to wake up a system using Wake-on-LAN (WoL) is also in place. If you want to wake a device that is not on your list, you can do so via the global settings menu. This is also where you can perform DNS lookups or run pings and traceroutes against any computer.
Fing is also useful as a security tool. For example, you can find out whether a router on the hotel WLAN uses client isolation (i.e., whether the individual devices can see each other) by running Fing. If you see other systems and services, you should transfer unencrypted data only after careful consideration.
Wifi Analyzer
Admins who are less interested in exploring the devices on their own networks and more interested in the wireless networks in the area should take a look at the classic Wifi Analyzer. The intuitive tool, which is suitable even for non-experts, scans all the wireless networks found in range and presents them in the channel overview as a colored graph (Figure 9), which can be helpful in analyzing reception problems or planning WLANs.
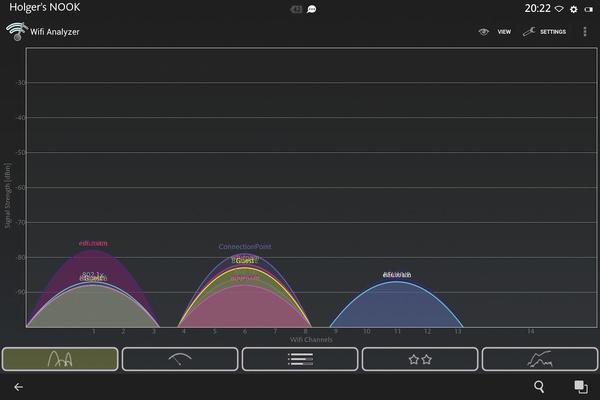
A needle graph shows the signal strength of an access point in real time, ranging from green (strong) to yellow to gray (weak). If you enable sound, the app can be used like a Geiger counter, giving you acoustic feedback on the quality of reception.
Interference Analysis
Channel evaluation also lets you operate your own wireless network on a channel that is as interference-free as possible. This process rates the individual channels with asterisks and helps to determine the least frequented channel, which is definitely a challenge in densely populated areas.
The AP list, which is designed more for technically interested users or for advanced debugging, gives you the names of the individual networks, channels used, frequencies, encryption type, and signal strength – and even the details of multiple available access points that share the same ESSID.
Apple: No Sniffers
In the iOS camp, the choice of applications has deteriorated significantly since Apple systematically began to remove sniffers from the App Store in mid-2010. The reason? Sniffers rely on unauthorized “private frameworks for spying on access and wireless data” (i.e., they tap the wireless chips directly, instead of using the library calls required by Apple).
However, applications that have their own WiFi database are still allowed; except it is of little use for exploring the wireless networks in your neighborhood. The only solution here is a jailbreak and detour via the alternative Cydia app store, which offers a wider selection of sniffers.
Administrators must decide for themselves whether root access is an alternative; many security experts advise it, quoting the motto, “if it is possible, do it yourself, rather than leave it to a hacker.” Nevertheless, this question is a matter for heated debate among security consultants.
If you are less concerned with individual devices but instead want to see the big picture, you will typically already have a monitoring solution like Nagios or Icinga in place. Matching apps and web interfaces are available for both, thus helping admins keep track of all their critical systems on a small screen. The Nagios website even names a number of mobile interfaces.
Conclusions
Smartphones and tablets with Android and iOS have advanced in recent years to the extent that they can be useful alternatives for admins when it comes to taking a quick look at a supervised system. Despite serious security deficiencies, they have lost their dubious reputation as admin tools. A wide selection of apps for virtually any application turns these mobile devices into general purpose tools – even without root permissions on the devices (see the box “More Fun with Root Privileges”).

The mobile admin’s backpack is becoming significantly lighter now that the laptop and PC can stay at home. However, for long sessions, it doesn’t hurt to have a laptop at hand – or at least a proper Bluetooth keyboard. Everything else is touch.
Info
[1] WiFinspect
[2] zAnti
[3] Android Forensics with Volatility and LiME
The Author

Holger Gantikow studied computer science at the University of Furtwangen and is a Senior Systems Engineer at Science + Computing in Tübingen, Germany. Holger deals with the complexity of heterogeneous systems in CAE computation environments and serves customers with technical and scientific applications.
Subscribe to our Linux Newsletters
Find Linux and Open Source Jobs
Subscribe to our ADMIN Newsletters
Support Our Work
Linux Magazine content is made possible with support from readers like you. Please consider contributing when you’ve found an article to be beneficial.

News
-
LibreOffice 26.2 Now Available
With new features, improvements, and bug fixes, LibreOffice 26.2 delivers a modern, polished office suite without compromise.
-
Linux Kernel Project Releases Project Continuity Document
What happens to Linux when there's no Linus? It's a question many of us have asked over the years, and it seems it's also on the minds of the Linux kernel project.
-
Mecha Systems Introduces Linux Handheld
Mecha Systems has revealed its Mecha Comet, a new handheld computer powered by – you guessed it – Linux.
-
MX Linux 25.1 Features Dual Init System ISO
The latest release of MX Linux caters to lovers of two different init systems and even offers instructions on how to transition.
-
Photoshop on Linux?
A developer has patched Wine so that it'll run specific versions of Photoshop that depend on Adobe Creative Cloud.
-
Linux Mint 22.3 Now Available with New Tools
Linux Mint 22.3 has been released with a pair of new tools for system admins and some pretty cool new features.
-
New Linux Malware Targets Cloud-Based Linux Installations
VoidLink, a new Linux malware, should be of real concern because of its stealth and customization.
-
Say Goodbye to Middle-Mouse Paste
Both Gnome and Firefox have proposed getting rid of a long-time favorite Linux feature.
-
Manjaro 26.0 Primary Desktop Environments Default to Wayland
If you want to stick with X.Org, you'll be limited to the desktop environments you can choose.
-
Mozilla Plans to AI-ify Firefox
With a new CEO in control, Mozilla is doubling down on a strategy of trust, all the while leaning into AI.
