The Kernel Self-Protection project aims to make Linux more secure
Canary vs. Overflow
A stack overflow overwrites parts of the stack. Protection can be provided by a canary, a bit sequence prior to the return address that the attacker cannot predict. If the patterns no longer match, that means somebody overwrote the stack. This is a warning, in the same way that a canary warned miners of mine gas.
A skillful attacker can work around this canary protection. For example, a technique called trampolining bends existing pointers in the program so that they point to the return address. However, this approach requires considerably more effort and the use of vulnerable pointers. Similarly, an attacker might try to read out the canary value and adjust the buffer overflow appropriately, but the programmer can counteract this step by randomizing the canary.
Shadow stacks provide a similar line of defense: They keep a copy of the return address, which the attacker is unlikely to access. The process checks whether the copy matches the original before it is returned [8].
The heap, as well as the stack, is sometimes vulnerable to overflows. Attackers often take advantage of use-after-free errors: The programmer releases memory with free(), but then uses the pointer again later on. Such errors can be corrected by more stringent checks when accessing memory areas in the kernel.
Invitation to Gamble
Attackers rely on well-known facts relating to the operating system's memory layout to inject their code (Figure 2). If the kernel randomizes the design of the addresses, attacking is like gambling. Although there are attacks like heap spraying, the overhead is growing. If both the kernel and the kernel modules are loaded at random addresses, and possibly in a random order, attacks on the kernel modules are more difficult. Similarly, random stack base addresses increase the effort required for a successful attack.
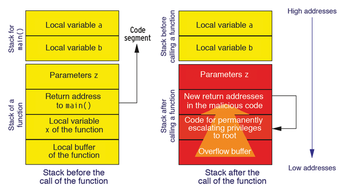
The more chance comes into play, the more important it is for the attacker to find out something about the memory structure or the value of canaries through information exposure. Attackers take advantage of the fact that released memory is usually not overwritten. Uninitialized variables or format string vulnerabilities also help.
To avoid this kind of information gathering, it is important to overwrite the memory immediately after releasing it. In addition, functions can be accessed via IDs and a table, analogous to the interrupt vector table, instead of directly using their addresses. This precaution means that the addresses outside the kernel are not known and are more difficult for attackers to predict.
Modular Is Cool
Attackers who have managed to inject malicious code in spite of the resistance usually look to install a rootkit, which they can do simply by loading their own kernel module into the system. To prevent this, the admin could compile the kernel statically – without module support – but a static kernel is often inconvenient, unless it is used with an embedded devices. Alternatively, the Self-Protection project suggests that only a few locally logged-in users should be allowed to load modules.
« Previous 1 2 3 Next »
Buy this article as PDF
(incl. VAT)
Buy Linux Magazine
Subscribe to our Linux Newsletters
Find Linux and Open Source Jobs
Subscribe to our ADMIN Newsletters
Support Our Work
Linux Magazine content is made possible with support from readers like you. Please consider contributing when you’ve found an article to be beneficial.

News
-
Canonical Releases Ubuntu 24.04
After a brief pause because of the XZ vulnerability, Ubuntu 24.04 is now available for install.
-
Linux Servers Targeted by Akira Ransomware
A group of bad actors who have already extorted $42 million have their sights set on the Linux platform.
-
TUXEDO Computers Unveils Linux Laptop Featuring AMD Ryzen CPU
This latest release is the first laptop to include the new CPU from Ryzen and Linux preinstalled.
-
XZ Gets the All-Clear
The back door xz vulnerability has been officially reverted for Fedora 40 and versions 38 and 39 were never affected.
-
Canonical Collaborates with Qualcomm on New Venture
This new joint effort is geared toward bringing Ubuntu and Ubuntu Core to Qualcomm-powered devices.
-
Kodi 21.0 Open-Source Entertainment Hub Released
After a year of development, the award-winning Kodi cross-platform, media center software is now available with many new additions and improvements.
-
Linux Usage Increases in Two Key Areas
If market share is your thing, you'll be happy to know that Linux is on the rise in two areas that, if they keep climbing, could have serious meaning for Linux's future.
-
Vulnerability Discovered in xz Libraries
An urgent alert for Fedora 40 has been posted and users should pay attention.
-
Canonical Bumps LTS Support to 12 years
If you're worried that your Ubuntu LTS release won't be supported long enough to last, Canonical has a surprise for you in the form of 12 years of security coverage.
-
Fedora 40 Beta Released Soon
With the official release of Fedora 40 coming in April, it's almost time to download the beta and see what's new.

