Analyzing a malicious Raspberry Pi Bash script
The Main Loop
First the script retroactively installs packages that are probably missing on a normal Raspberry Pi, including ZMap [6] and SSHPass [7] (lines 133-134). ZMap is a network scanner optimized to scan the IPv4 address space for a specific port. A commercially available PC with a symmetrical 1Gbps Internet connection requires about 45 minutes for a complete scan. A 10Gbps connection with corresponding hardware (typically a Linux cluster) and an optimized TCP/IP stack (with PF_RING [8], a network socket for capturing packets) takes about five minutes [6].
In line 138, a random 100,000 IP addresses are scanned for port 22 availability. The average hit rate is just under 0.6 percent. In these two cases, zmap on two cores of a Raspberry Pi 3B (RPi3B) took about 23 seconds to call.
The propagation is carried out in lines 141 and 142. This code tries to copy the script with scp. When logging in, the script uses the default password raspberry or the password of the Linux.MulDrop.14 miner. If successful, the IP address is stored in the /opt/.r file. The malware then makes the copied file executable on the freshly hacked computer and starts it.
To set a password for SSH in a script, you need the sshpass wrapper, which spoofs an interactive password entry for SSH. Production use of SSHPass is risky: Automation with a certificate-based logon and an SSH key agent seems more appropriate.
Table 1 shows the total number of scanned IP addresses, the number of reachable SSH ports, and the number of successful logins with one of the two passwords. The run time of a loop pass depends on the network interface used. In both cases, the target was an RPi3B.
Table 1
Success Statistics
| RPi3B | No. Scanned | SSH Matches | Rasp Pi Matches | Run Time (min:sec) |
|---|---|---|---|---|
| 1 |
20.3 x 10^6 |
81,770 |
6 |
2:30 (wlan0) |
| 2 |
78.4 x 10^6 |
(Unknown) |
33 |
1:05 (eth0) |
On the first RPi3B, the admins were able to determine the number of IP addresses found with SSH service, because a line in /var/log/syslog was added to each (also unsuccessful) login (Listing 3). The UserKnownHostsFile script redirects to /dev/null (Listing 1, lines 141 and 142), so this entry is visible for each of the two logins, because the file is always empty when read. The duplicates were removed when counting the IP addresses, thus determining the number of SSH servers found. No log entries existed for the second RPi3B.
Listing 3
Log Entries
If the attacker finds a normal SSH server during these login attempts, two unsuccessful logins occur, because only the first command up to the first && is executed (line 141). These duplicate login attempts from the same IP address within one second are a clear signature of this script.
The IRC Bot
Although considered old-fashioned, this script creates a backdoor for remote control of the hijacked Raspberry Pi via IRC. The remote control feature doesn't seem to work anymore because the IRC channel #biret is disabled.
This IRC script connects to a randomly selected IRC server from six options and sets its nickname to a value calculated from the output of uname -a. The communication in /tmp/bot.log is logged in line 123. The provider Undernet manages one of the largest ICQ networks [9] but has nothing to do with the malware.
Line 73 creates file descriptor 3 for writing and reading to the specified TCP socket (e.g., /dev/tcp/ix1.undernet.org/6667 if the first server is selected). Thus, it is very easy to script communication to a server with simple printf and read commands.
The script reacts to the IRC PING commands with a PONG (lines 93-101) and connects to the biret IRC channel (line 99). It also responds to private messages (PRIVMSG, lines 102-105) that contain Base64-encoded commands. The command is copied to privmsg_data, and a digital signature to privmsg_h.
The script then compares the MD5 checksum of the decoded command (hash) with the decrypted checksum from the signature (sign). The command only starts if the digital signature is OK (line 110). The result of the execution is returned with Base64 encoding.
Evaluating the Logfiles
If you evaluate the numerous Invalid user pi from … log entries, you can determine the total number of invalid attempts, as well as the number of duplicate login attempts from one IP address at an interval of less than one second (hereafter referred to as pairs), which is the signature of this script.
An initial evaluation of the logfiles from three computers partially used as honeypots in the time window from August 5 to September 4, 2018 (31 days) is shown in Table 2. Between 1.5 and 2.5 events per IP address and day indicate that the script is still busy scanning.
Table 2
Attacks on Honeypots
| Computer | Logins | Pairs | Pairs/Day |
|---|---|---|---|
| DSL connection |
184 |
84 |
2.7 |
| RZ Netcup |
140 |
64 |
2.1 |
| RZ 1&1 |
128 |
48 |
1.5 |
Next, I evaluated two different log datasets. The first collected all invalid SSH login attempts with username pi between April 13, 2013, and September 7, 2018, for a single server. The second record contained invalid SSH login attempts with username pi on the servers of a research institution from November 25, 2018, 3:27am, to November 27, 2018, 11:35am (i.e., for 56 hours and 8 minutes). All told, invalid logins on 188 different computers in this institution were attempted. The first setting had 4,156 entries (Figure 2), of which 1,025 were pairs. The first pair appeared on June 10, 2017, which meant that pairs appeared here in a time window of 455 days at an average of 2.2 per day.
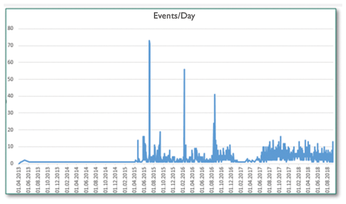
The login attempts came from 799 different IP addresses. However, the three events with a strongly increased number of login attempts in July 2015, February 2016, and August 2016 can no longer be analyzed retrospectively because of a lack of data from this time.
Before April 2015, practically no invalid login attempts were made (fewer than 12 per year) with the pi account. Activity increased around June 2017. A closer look at this time window shows the first signatures of the pair script (Listing 4) from June 10, 2017.
Listing 4
Pairs
The second setting experienced 2,022 entries in 56 hours, of which 660 were pairs, corresponding to 11.8 pairs per hour, 3.5 pairs per server, or 1.5 pairs per server per day. The login attempts came from 267 different IP addresses.
« Previous 1 2 3 Next »
Buy this article as PDF
(incl. VAT)
Buy Linux Magazine
Subscribe to our Linux Newsletters
Find Linux and Open Source Jobs
Subscribe to our ADMIN Newsletters
Support Our Work
Linux Magazine content is made possible with support from readers like you. Please consider contributing when you’ve found an article to be beneficial.

News
-
TUXEDO Computers Unveils Linux Laptop Featuring AMD Ryzen CPU
This latest release is the first laptop to include the new CPU from Ryzen and Linux preinstalled.
-
XZ Gets the All-Clear
The back door xz vulnerability has been officially reverted for Fedora 40 and versions 38 and 39 were never affected.
-
Canonical Collaborates with Qualcomm on New Venture
This new joint effort is geared toward bringing Ubuntu and Ubuntu Core to Qualcomm-powered devices.
-
Kodi 21.0 Open-Source Entertainment Hub Released
After a year of development, the award-winning Kodi cross-platform, media center software is now available with many new additions and improvements.
-
Linux Usage Increases in Two Key Areas
If market share is your thing, you'll be happy to know that Linux is on the rise in two areas that, if they keep climbing, could have serious meaning for Linux's future.
-
Vulnerability Discovered in xz Libraries
An urgent alert for Fedora 40 has been posted and users should pay attention.
-
Canonical Bumps LTS Support to 12 years
If you're worried that your Ubuntu LTS release won't be supported long enough to last, Canonical has a surprise for you in the form of 12 years of security coverage.
-
Fedora 40 Beta Released Soon
With the official release of Fedora 40 coming in April, it's almost time to download the beta and see what's new.
-
New Pentesting Distribution to Compete with Kali Linux
SnoopGod is now available for your testing needs
-
Juno Computers Launches Another Linux Laptop
If you're looking for a powerhouse laptop that runs Ubuntu, the Juno Computers Neptune 17 v6 should be on your radar.

